
In February of this year, a man was
arrested at the British airport who was suspected of carrying out a large number of powerful DDoS attacks on networks of many organizations. Among the victims are French hosting provider OVH and
Dyn , which provides network infrastructure for companies and services such as Twitter, Amazon, Tumblr, Reddit, Spotify and Netflix. Also, the botnet attacked equipment and services of Deutsche Telekom, Eircom, TalkTalk, UK Postal Office and KCOM.
They tried to prove the guilty of the detainee for several months. The police gradually unwound the tangle, received new information and in the end received the recognition of the arrested person himself. In February, his name was not reported, but now it became known that his name is Daniel Kaye. He is 29 years old, he is a citizen of Great Britain. As previously reported, it was he who managed the modified version of Mirai, which was able to attack routers through port 7547, working with the TR-064 and TR-069 protocols for this.
After the arrest of the attacker was extradited to Germany. Here, a few days ago, he admitted to the crime, saying, however, that he was not going to stop the work of the provider of Deutsche Telekom at all, but only wanted to strengthen his botnet by commissioning the infected routers of the company. During this attack, something went wrong and thousands of network devices started to turn off. This was the reason for online blackouts in Germany and other countries. Naturally, large-scale outages of the network infrastructure of entire countries caused huge losses for a number of companies.
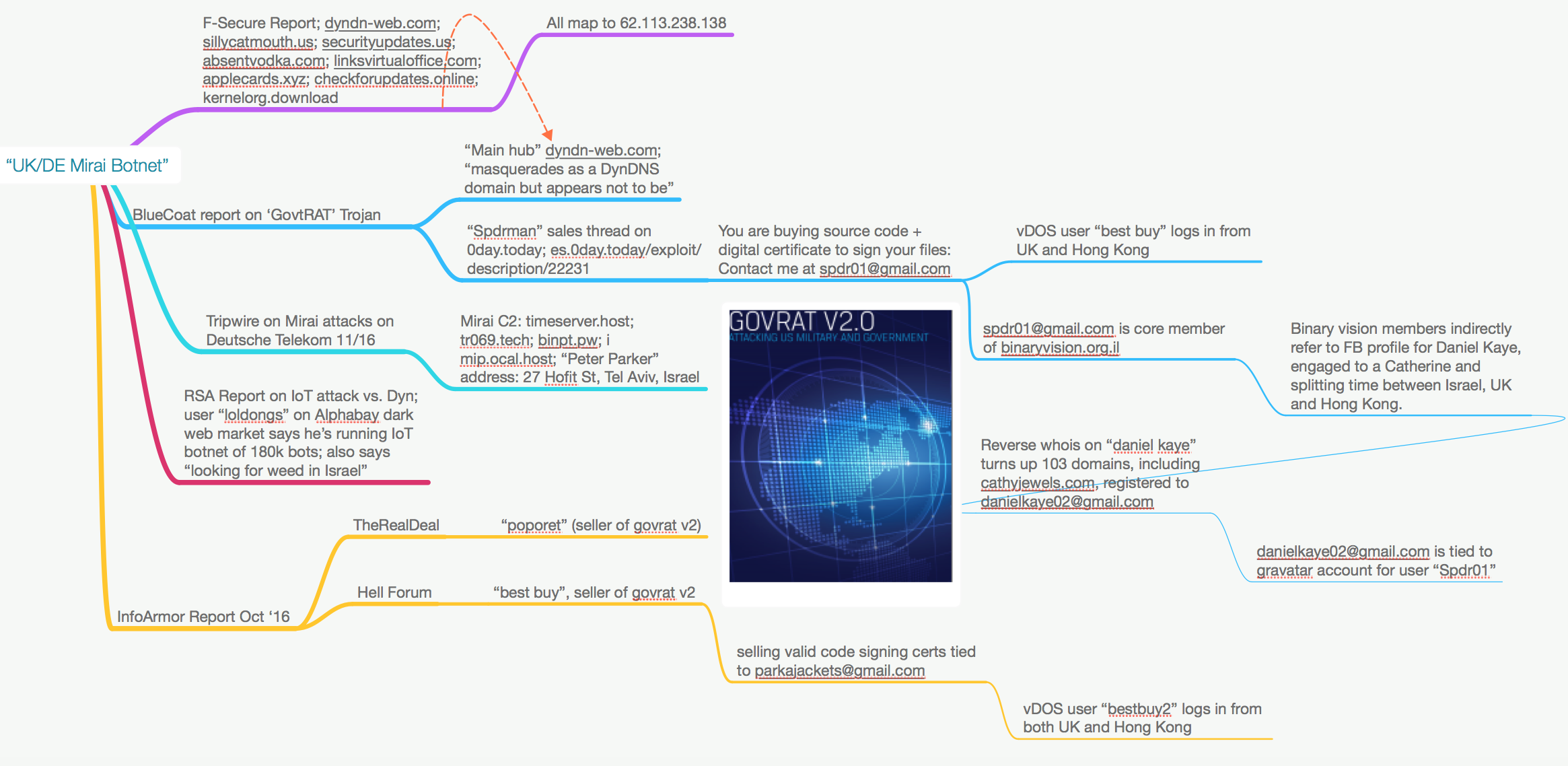 “Thought Card” that Krebs used during his own investigation
“Thought Card” that Krebs used during his own investigationThe cybercriminal said that he worked not only on his own, pursuing his own goals, but also fulfilled the orders of third-party companies, for example, a Liberian Internet provider who wanted to influence competitors in some way or another in a negative way. For the execution of the order, the organization’s management paid the attacker $ 10,000.
It is worth noting that the arrest of the offender is a considerable merit of Brian Krebs (Brian Krebs), a specialist in network security. By the way, it was he who was one of the first to suffer from the actions of the Mirai botnet - his blog did not work for a while.
A German court found the attacker guilty of many counts, but gave only a suspended sentence without putting him in jail. Interestingly, Kaye is not only a botnet operator who deftly took control in due time, taking it into his own hands, but also the author of the GovRAT software platform, which allows users to perform quite complex tasks of implementing various financial, state and military organizations stealing funds and information. At the moment, it is known that this particular software “lit up” in 100 cases of cyber attacks.
 Fragment of Daniel Kaye's Facebook page
Fragment of Daniel Kaye's Facebook pagePerhaps the court took into account that the young cybercriminal repented completely, telling that all his actions were a huge mistake that he would like to correct and would never like to repeat. He also stated that he had committed crimes in order to earn money for life with his girlfriend, with whom he had connected life. The conditional term turned out not too long - only a year and
eight months .
Nevertheless, despite the fact that Kaye received such a mild sentence in Germany, he could still face a real prison sentence in the UK, where he is still under investigation. And the authorities have already requested the extradition of the offender.
Brian Krebs says in his article that so far none of the cybercriminals involved in the creation or management of the Mirai botnet has been seriously punished. The software platform itself, which allowed to infect IoT devices, and which was the beginning of the entire chain of hacks and DDoS attacks, was developed by the programmer Paras Jha. The identity of this man, hiding under the name Anna Sepai,
also revealed Brian Krebs . He himself has twice been the victim of the Mirai botnet's DDoS attacks. He quickly got tired of it, and the journalist started his own investigation. Probably it was not worth the attackers trying to "punish" Krebs, in the end they themselves dug a hole. True, the pit was not so deep.