
Any computer or server needs, for full functioning, not only high-quality hardware, but no less high-quality and, most importantly, secure software. Today we will look at some of the statistics telling which OSs are the most vulnerable, which are more secure, and which particular vulnerabilities in each of them were seen most often.
In order to avoid the incredible longrid this material will be divided into 4 parts. Each of which will describe the vulnerability of 5 operating systems. In the first, I mean in this part, we will consider the first 5 participants of our rating, based on data for 2017.
| OS name | Manufacturer | Total number of vulnerabilities for 2017 | Total number of vulnerabilities for 2016 | The total number of vulnerabilities for all time statistics |
|---|
| Android | Google | 666 | 523 | 1357 |
| Linux Kernel | Linux | 381 | 217 | 1921 |
| Iphone os | Apple | 293 | 161 | 1277 |
| Windows 10 | Microsoft | 226 | 172 | 451 |
| Windows Server 2016 | Microsoft | 212 | 39 | 251 |
| Windows Server 2008 | Microsoft | 212 | 133 | 981 |
| Mac os x | Apple | 210 | 215 | 1888 |
| Windows Server 2012 | Microsoft | 201 | 156 | 606 |
| Windows 7 | Microsoft | 197 | 134 | 838 |
| Windows 8.1 | Microsoft | 192 | 154 | 542 |
| Windows RT 8.1 | Microsoft | 124 | 139 | 438 |
| Debian linux | Debian | 95 | 327 | 1029 |
| Fedora | Fedora project | 84 | 120 | 441 |
| Ubuntu linux | Canonical | 66 | 279 | 867 |
| Watchos | Apple | 65 | 77 | 231 |
| Windows vista | Microsoft | 64 | 125 | 814 |
| Opensuse | Opensuse project | 58 | five | 119 |
| Leap | Opensuse project | 57 | 2 | 60 |
| Leap | Novell | 48 | 260 | 349 |
| XEN | XEN | 44 | 28 | 228 |
First of all, it should be noted that these statistics can be interpreted in different ways, since there are several discrepancies with the participants' initial data - first of all, their age (some OS exists 5 years, some only a year), therefore common the data for the entire period of their existence should not be taken into consideration in a comparative analysis, but should be taken into account as general data. Although, on the other hand, when the young OS has more vulnerabilities than the one that has been in existence for many years, this leads to certain thoughts.
The leader of our anti-rating for 2017 and 2016 was Android with the results of 666 and 523 vulnerabilities, respectively. In the meantime, when statistics were collected and processed, the Linux kernel (the basis of the Linux operating system family) has been leading since 1921 vulnerabilities.
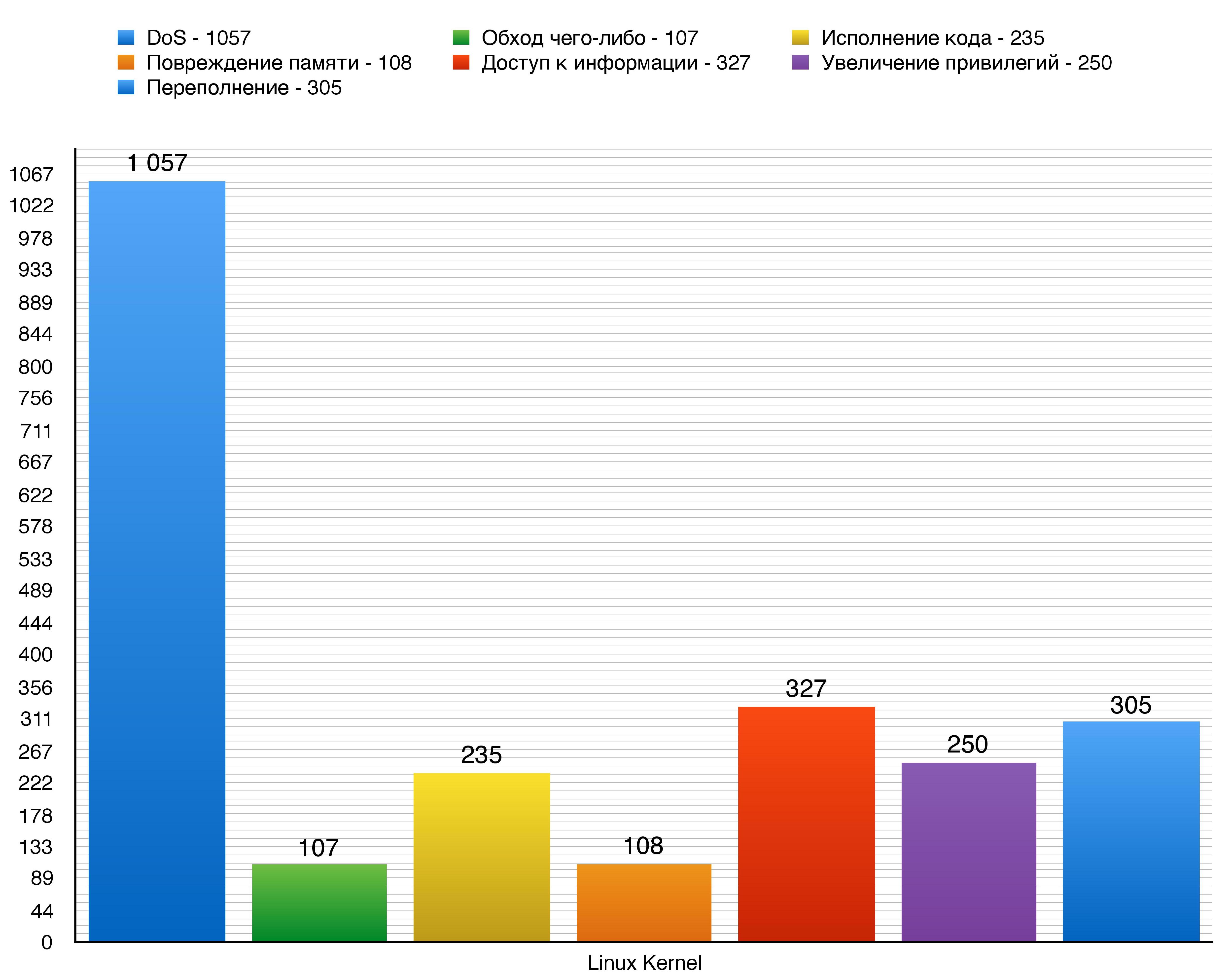
Vulnerabilities are many, as we see, hundreds or even thousands. Here are the main types of vulnerabilities that are considered in our analysis:
- DoS (Denial of Service / Denial of Service) (exploit of vulnerability leads to DoS devices);
- Bypassing something (for example, a password to enter the system);
- Execution of the code (the ability of the attacker to execute some command on the victim's device);
- Memory damage;
- Access to information (referring to secret information obtained through vulnerability);
- Privilege escalation (particularly for malware);
- Overflow (buffer);
It is worth considering more closely some of the vulnerabilities seen on one or another OS. The CVE Details portal scores each of them. The number of points depends on the level of damage and mass distribution. The maximum indicator is 10 points. It is about such vulnerabilities (if they exist and if they are unique) that will be discussed further. In order for this article not to become Lenin’s five-volume, we will focus only on three vulnerabilities from the list, which may contain hundreds of items.
Description of the tablesIn the tables of each of the types of vulnerabilities, certain additional parameters are indicated for a particular vulnerability. More about them.
Impact level1)
confidentiality :
- Full - the vulnerability allows attackers to access all information on the device;
- Partial - significant disclosure;
- None - privacy is not violated;
2)
integrity :
- Full - the integrity of the system is completely compromised, the complete loss of system protection;
- Partial - modification of some system files or information is possible, but the attacker has no control over what can be changed;
- None - no impact on the integrity of the system;
3)
availability :
- Full - the vulnerability allows an attacker to completely block access to the resource;
- Partial - performance degradation or intermittent availability of resources;
- None - no impact on system availability;
Difficulty of access- Low - no special conditions for access are required, as well as no specific knowledge or skills are required;
- Medium - some conditions must be met to gain access;
- High - special access conditions limiting the exploit;
Authentication- Not required - authentication is not required for the exploit of the vulnerability;
- Single system - the vulnerability requires the hacker to be logged into the system (for example, via the command line, desktop mode or via the web interface).
And now, after we have read the general data and figured out what and how will be in the tables below, let's move on to a specific consideration of each of the five operating systems.
1. Android
 Android
Android - OC for smartphones, tablets, game consoles, etc. The first appearance is 2008. The total number of users for the entire existence of about 2 billion people. This figure is amazing. And as we know, the more common the software is, the more carefully the attackers will study its flaws and holes for further use in their dark deeds. The debate on Android OS security has been going on for a very long time. Someone considers it the worst, someone argues that for the average user-philistine, this OS is quite suitable and its shortcomings are almost not felt. However, opinions are opinions, and numbers can say much more.
 DoS
DoS10 points deserved 61 vulnerabilities out of 253.
Vulnerability # 1On Samsung Galaxy S4-S7 devices, there is a software overflow in libomacp.so during parsing (parsing)
OMACP (in
WAP Push SMS messages ), which causes
heap corruption, which can lead to DoS and remote code execution.
OMACP is a system application for displaying partial message content on a device screen (preview).
WAP Push SMS is a special SMS format containing links for easy activation.
A heap is a data structure of the tree type.
Vulnerability # 2Multiple software overflows in the MDSS driver for the Linux 3.x kernel, which is used in MSM Android devices from the Qualcomm Innovation Center (QuIC), allows attackers to organize DoS and conduct other malicious actions.
Vulnerability # 3DRMExtractor.cpp in the libstagefright library of the mediaserver component on Android devices does not check some offset data, which allows an attacker to do DoS, execute code, or corrupt memory by adding the media file created by him.
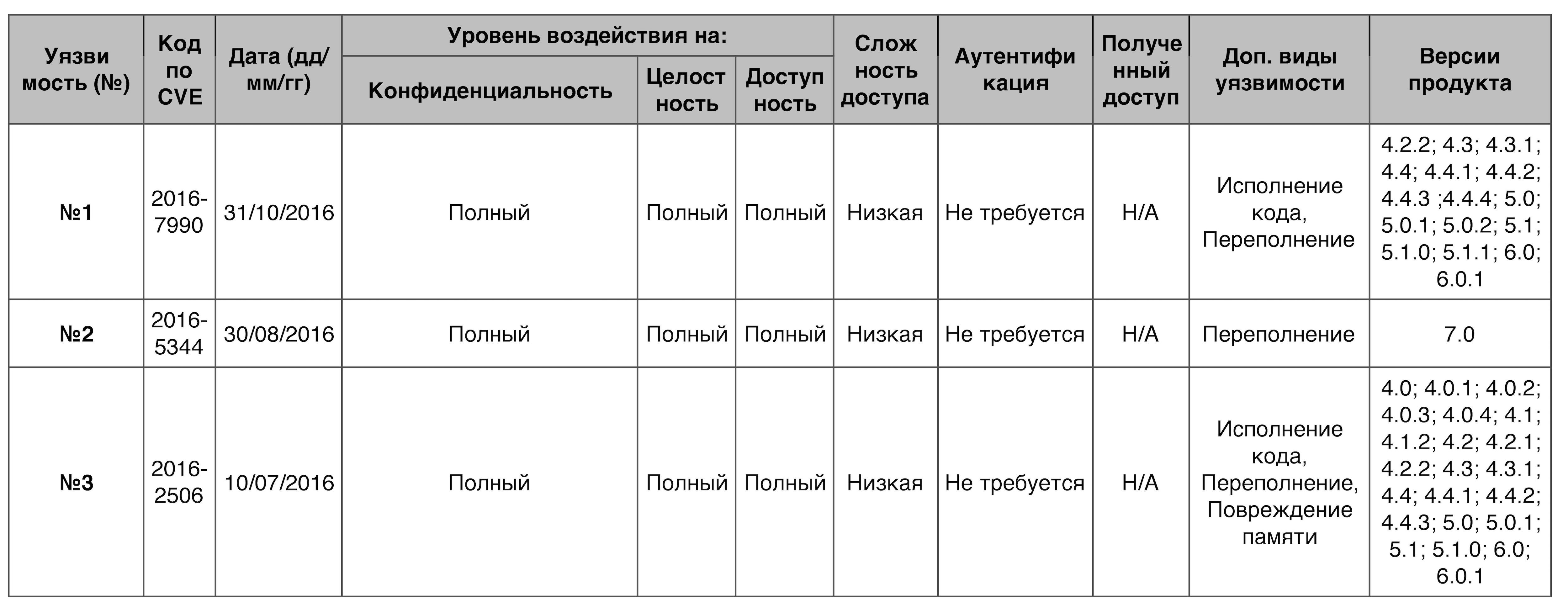 Table of vulnerabilities category "DoS" in the Android OSBypassing something
Table of vulnerabilities category "DoS" in the Android OSBypassing something5 cases out of 104 scored 10 points.
Vulnerability # 1app / aboot / aboot.c in Qualcomm components on Nexus 5 devices running on Android OS incorrectly checks the overflow integrity, which allows attackers to bypass established access restrictions using the generated “start” and size values.
Vulnerability # 2The libs / gui / BufferQueueConsumer.cpp in mediaserver in Android does not check the android.permission.DUMP permission, which allows attackers to obtain confidential information and, therefore, bypass unspecified protection mechanism, by requesting a dump, as evidenced by signing or SignatureOrSystem.
Vulnerability # 3media / libmedia / IOMX.cpp in mediaserver in Android does not initialize the data structure parameter, which allows attackers to obtain confidential information from the process memory and, as a result, bypass unspecified protection mechanisms through undefined vectors, as evidenced by signing or SignatureOrSystem.
 Vulnerability Table "Crawl" category in Android OSCode execution
Vulnerability Table "Crawl" category in Android OSCode execution80 cases out of 346 scored 10 points.
Vulnerability # 1On Samsung Galaxy S4-S7 devices, there is a software overflow in libomacp.so during parsing (parsing) OMACP (in WAP Push SMS messages), which causes heap corruption, which can lead to DoS and remote code execution.
Vulnerability # 2The vulnerability of remote code execution in the Qualcomm crypto driver could lead to a remote attack with the execution of arbitrary code in the context of the kernel.
Vulnerability # 3The udp.c in the Linux kernel up to version 4.5 allows you to remotely execute arbitrary code through UDP traffic, which starts the unsafe calculation of the second checksum during the execution of the recv system call with the MSG_PEEK flag.
 Code Execution Vulnerability Table for Android OSMemory damage
Code Execution Vulnerability Table for Android OSMemory damage57 cases out of 118 - 10 points.
Vulnerability # 1libAACdec / src / aacdec_drc.cpp in mediaserver on Android devices incorrectly limited the number of threads, which allowed remotely to execute arbitrary code or organize DoS, by adding a media file created by the attacker.
Vulnerability # 2The libFLAC / stream_decoder.c in the mediaserver Android devices did not prevent free operations with uninitialized memory, which allowed the hacker to execute arbitrary code or DoS through the media file added by him.
Vulnerability # 3DRMExtractor.cpp in the libstagefright library of the mediaserver component on Android devices does not check some offset data, which allows an attacker to do DoS, execute code, or corrupt memory by adding the media file created by him.
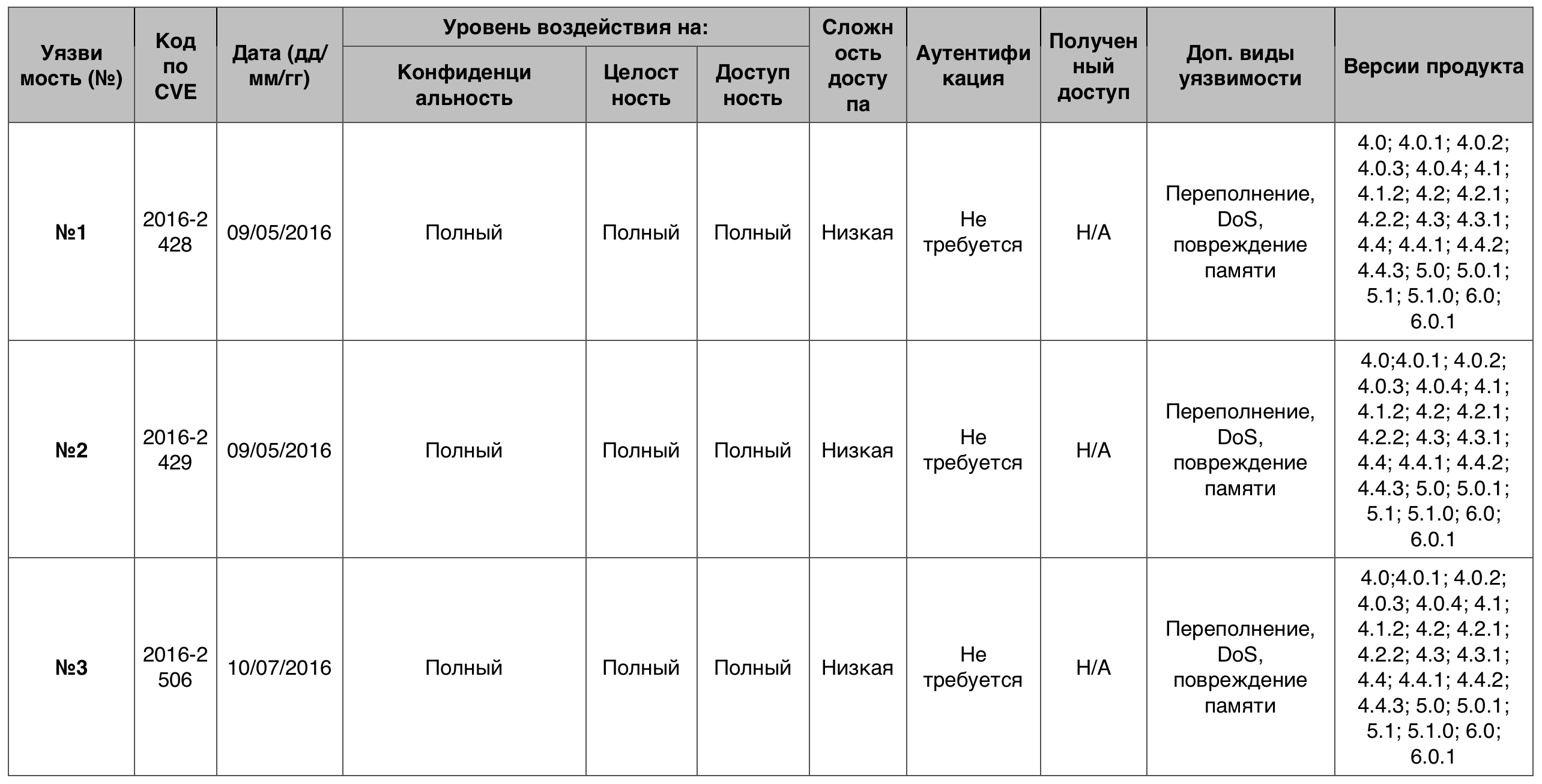 Table of vulnerabilities category "memory damage" in the Android OSAccess to the information
Table of vulnerabilities category "memory damage" in the Android OSAccess to the informationOnly 4 cases out of 210 scored 10 points.
Vulnerability # 1media / libmedia / IOMX.cpp in mediaserver on Android devices does not initialize the parameter data structure, which allows an attacker to gain access to valuable information from the process memory, and, subsequently, to bypass unspecified mechanisms sewn through undefined vectors, as evidenced by accessing a signature or SignatureOrSystem.
Vulnerability # 2media / libmedia / IOMX.cpp in mediaserver on Android devices does not initialize certain pointers of the metadata buffer, which allows an attacker to gain access to valuable information from the process memory, and, subsequently, to bypass unspecified mechanisms sewn through undefined vectors, as evidenced by accessing the signature or SignatureOrSystem.
Vulnerability # 3media / libmedia / IOMX.cpp in mediaserver on Android devices does not initialize a specific key request data structure, which allows an attacker to gain access to valuable information from the process memory, and, subsequently, bypass unidentified mechanisms sewn through undefined vectors, as indicated by access Signature or SignatureOrSystem.
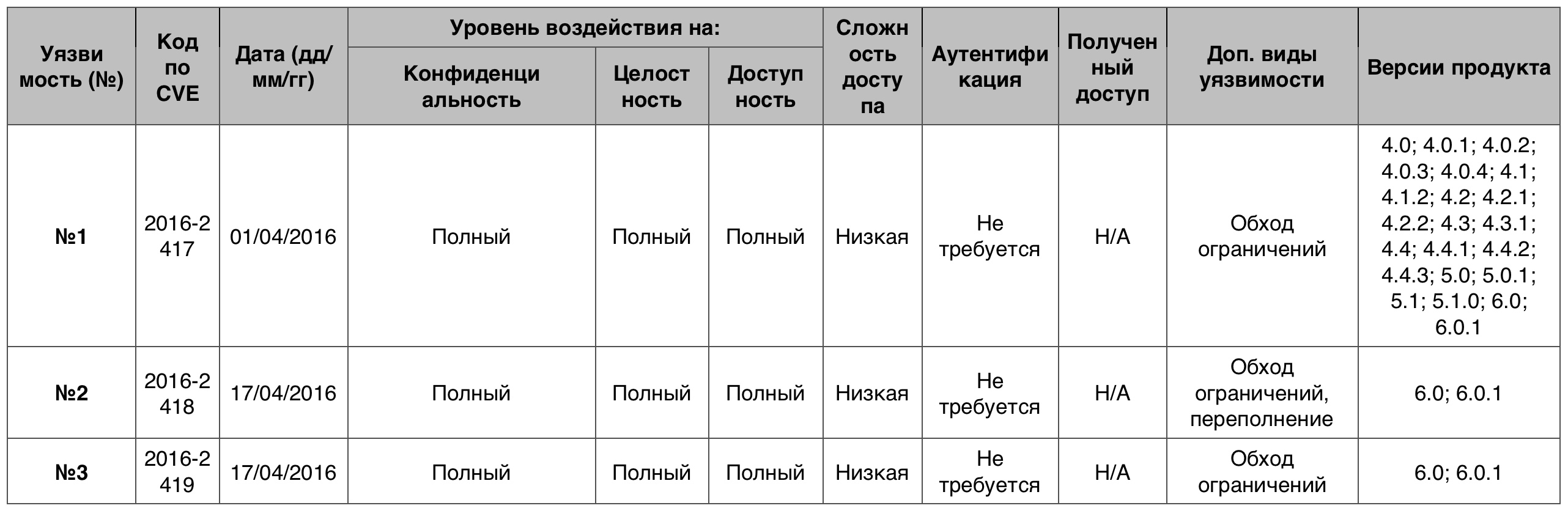 Table of vulnerabilities of the category "Access to Information" in the Android OSPrivilege increase
Table of vulnerabilities of the category "Access to Information" in the Android OSPrivilege increase6 cases out of 310 - 10 points.
Vulnerability # 1Privileges increased their privileges through a vulnerability in mediaserver on Android devices version 4.0.3 - 5.x, up to version 5.1.
Vulnerability # 2Multiple software overflows in the GraphicBuffer :: unflatten function in platform / frameworks / native / libs / ui / GraphicBuffer.cpp allowed attackers to get privileges or run DoS through a vector that activates a large number of file descriptors or integer values.
The file descriptor is a non-negative integer. When creating a new I / O stream, the kernel returns its file descriptor to the author process.
Vulnerability # 3The use
-after-free vulnerability in the venc mm-video-v4l2 component in the mediaserver allowed attackers to gain privileges through the application they created, as evidenced by the receipt of signature access or SignatureOrSystem.
Use-after-free is a type of memory damage vulnerability. Indicates the use of device memory after it is released (cleaned).
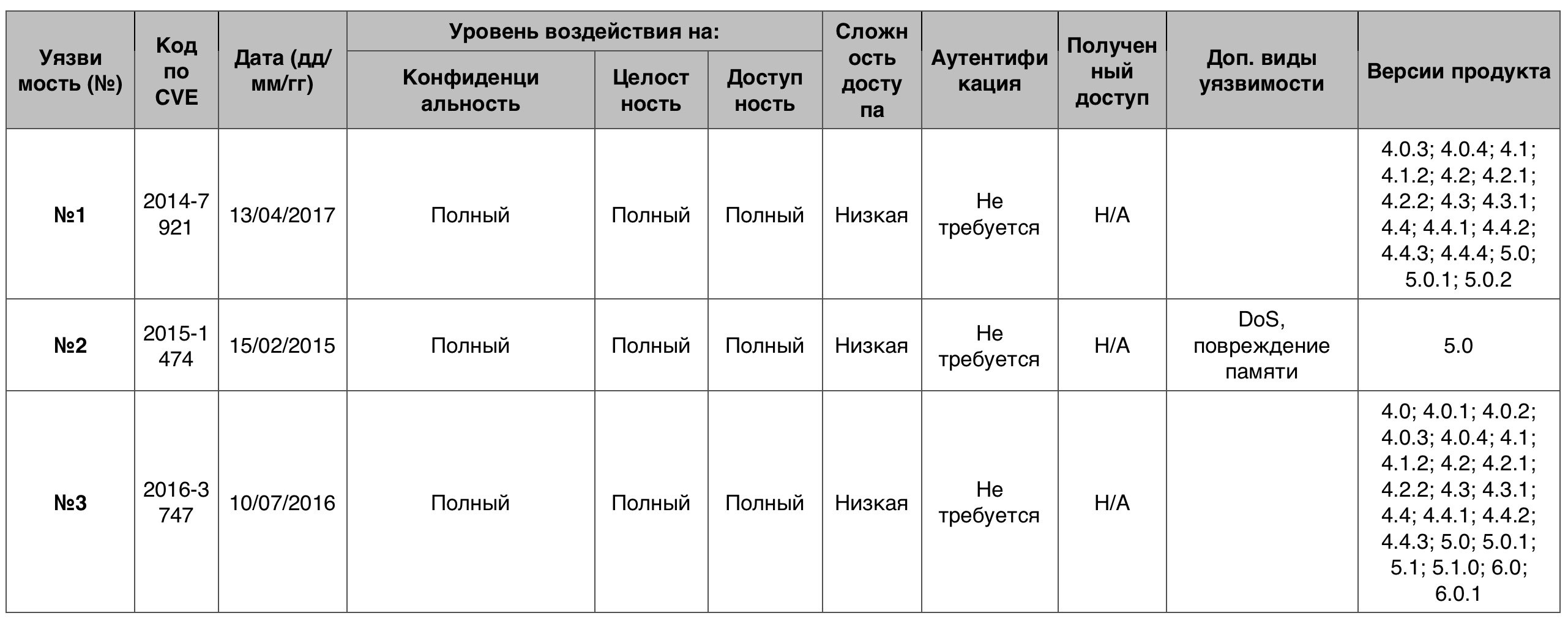 Privilege Increase vulnerability table in Android OSOverflow
Privilege Increase vulnerability table in Android OSOverflow100 cases out of 289 - 10 points.
Vulnerability # 1All Qualcomm Android-based products from CAF using the Linux kernel had a merge error ssl with ClientHello, which resulted in a memory leak.
Vulnerability # 2All Qualcomm-based Android products from CAF using the Linux kernel had software overflow in the hypervisor.
Vulnerability # 3In all Qualcomm Android-based products from CAF using the Linux kernel, the driver could potentially lead to a memory leak.
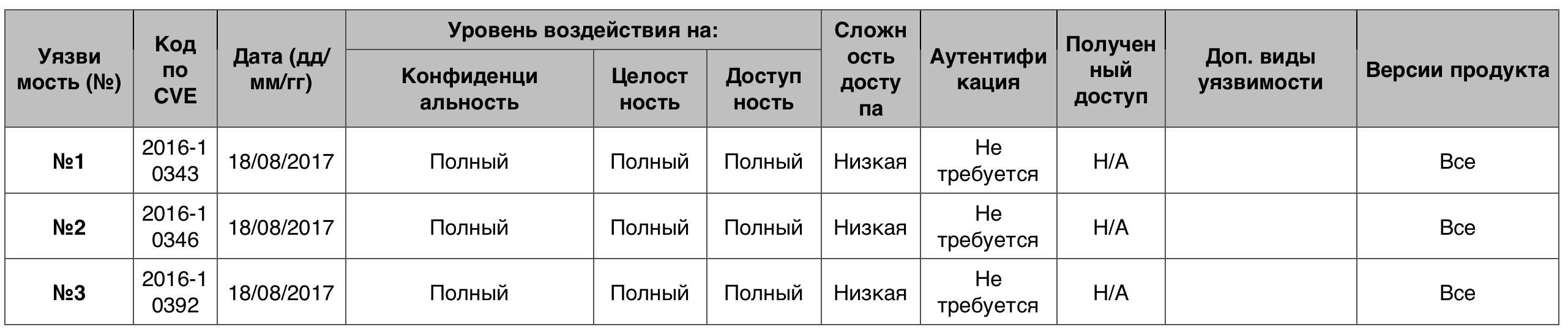 Table of vulnerabilities category "Overflow" in the Android OS
Table of vulnerabilities category "Overflow" in the Android OSThe number of vulnerabilities in the Android OS is still quite large. Moreover, most of them provide attackers with either full or partial access to the device and its data. And this can lead to loss of data or even loss of funds, given the fact that mobile devices are often used to verify entry into banking and payment systems.
2. Linux Kernel
 Linux Kernel
Linux Kernel is the core of the operating system, the basis of the Linux family of operating systems. In other words, these are the insides of the OS, while the outer shell may be different. First appearance - 1991. Despite the large number of vulnerabilities discovered from 1999 to 2017, Linux is not as popular among cybercriminals. And everything is connected with its small distribution in the world. According to some data, only 1% of the total number of computer users use this particular OS. And for more profit hackers need more victims.
 DoS
DoS23 vulnerabilities out of 1070 scored 10 points.
Vulnerability # 1The inet_csk_clone_lock function in net / ipv4 / inet_connection_sock.c allows attackers to organize DoS by controlling the received system call.
Vulnerability # 2The mq_notify function in the Linux kernel does not set the socket pointer to NULL when entering repeat mode. While the
Netlink socket is closed by user space, attackers can organize DoS.
Netlink is a Linux kernel interface for establishing communication between user processes and processes of the kernel itself.
Vulnerability # 3The __skb_flow_dissect function in net / core / flow_dissector.c does not make sure that n_proto, ip_proto and thoff are initialized, which allows you to arrange DoS or execute arbitrary code through the created MPLS packet.
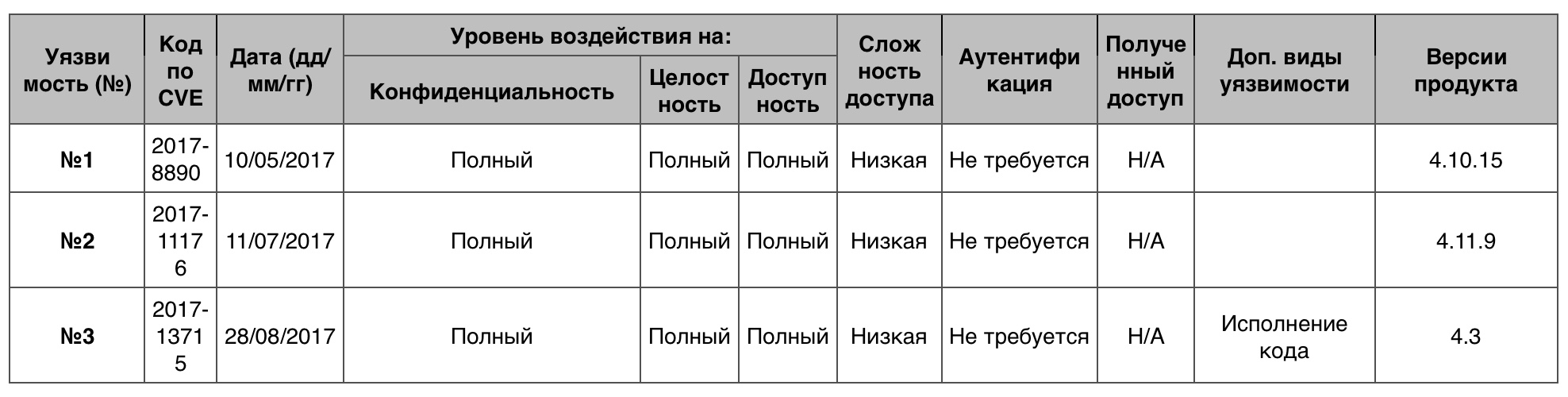 Table of vulnerabilities category "DoS" in the Linux kernelBypassing something
Table of vulnerabilities category "DoS" in the Linux kernelBypassing somethingSince only 1 vulnerability earned 10 points, we will consider (besides it) two cases following it.
Vulnerability # 1 (10)Software overflow leads to a
TOCTOU state in the PIL (Peripheral Image Loader) hypervisor, which also causes
a race condition , which can be used to bypass authentication in the PIL.
TOCTOU - Time of check to use - class of bugs caused by changes in the system between the state check (for example, login credentials) and the use of the results of this check.
Race condition - a design error of a multi-threaded system or application, when the operation of the system or application depends on the order of code execution
Vulnerability # 2 (9.3 points)arch / arm64 / kernel / sys.c in the Linux kernel up to version 4.0 allowed users to bypass the “strict page permissions” protection mechanism and modify the system calls table, subsequently gaining privileges by exploiting write access.
Vulnerability # 3 (9.3 points)The vulnerability of information disclosure in the Qualcomm bootloader could allow local malware to execute arbitrary code in the context of the bootloader.
 Vulnerability Table "Crawl" category in the Linux kernelCode execution
Vulnerability Table "Crawl" category in the Linux kernelCode execution11 vulnerabilities (10 points) out of 236 in all.
Vulnerability # 1udp.c in the Linux kernel version 4.5 allows you to remotely execute arbitrary code via UDP traffic, which starts the unsafe calculation of the second checksum during the execution of the recv system call with the MSG_PEEK flag.
Vulnerability # 2Vulnerability in the Broadcom Wi-Fi firmware made it possible to remotely execute arbitrary code inside the Wi-Fi SoC context.
Vulnerability # 3The __skb_flow_dissect function in net / core / flow_dissector.c does not make sure that n_proto, ip_proto and thoff are initialized, which allows you to arrange DoS or execute arbitrary code through the created MPLS packet.
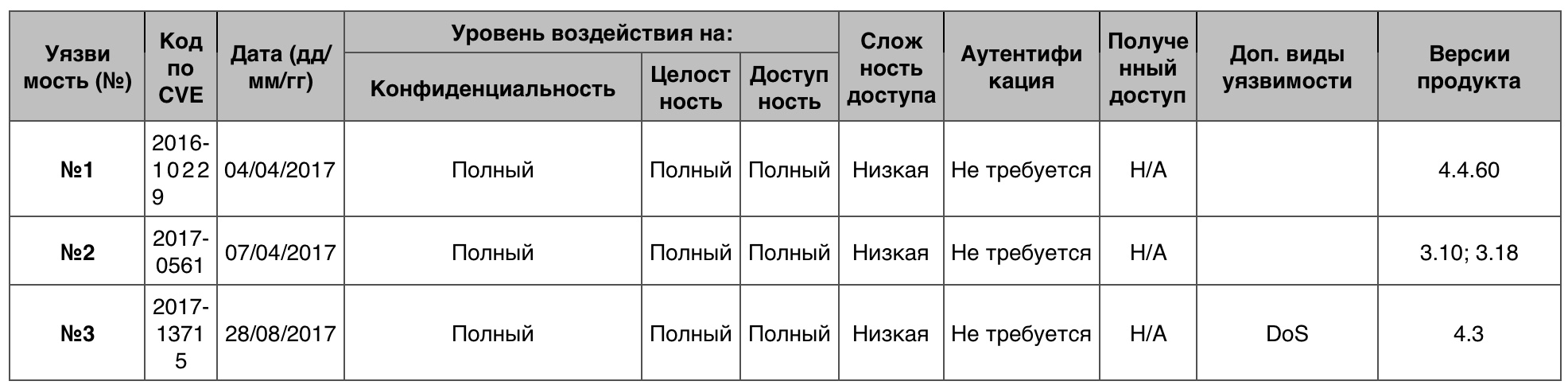 Table of Code Execution vulnerabilities in the Linux kernelMemory damage
Table of Code Execution vulnerabilities in the Linux kernelMemory damage3 vulnerabilities (10 points) out of 109 total.
Vulnerability # 1The buffer overflow in RNDIS USB implementation made it possible to arrange DoS via a remote NDIS response to the OID_GEN_SUPPORTED_LIST, which resulted in memory allocation for the response data, rather than its structure.
Vulnerability # 2A software error in the CIFSFindNext function in fs / cifs / cifssmb.c allowed remote CIFS servers to create DoS through a large length value in response to a directory read request.
Vulnerability # 3sound / soc / msm / qdsp6v2 / msm-audio-effects-q6-v2.c in the MSM QDSP6 sound driver for the Linux 3.x kernel used in MSM Android devices from Qualcomm Innovation Center (QuIC), made it possible to organize DoS through the created application that caused
ioctl to cause improper use of the parameter pointer.
ioctl is a system call for I / O and other operations that cannot be handled by regular system calls.
 Table of vulnerabilities category "memory corruption" in the Linux kernelAccess to the information
Table of vulnerabilities category "memory corruption" in the Linux kernelAccess to the informationAt the moment, there were no vulnerabilities that could be assessed at 10 points, therefore we consider those that exist.
Vulnerability # 1 (9.3)The vulnerability of information disclosure in the Qualcomm bootloader could allow local malware to execute arbitrary code in the context of the bootloader.
Vulnerability # 2 (8.5)The OZWPAN driver relies on an unreliable attribute during packet parsing, which allows DoS and access to valuable information from the kernel memory at the expense of the created package.
Vulnerability # 3 (7.9)Up to version 2.6.35, the implementation of xfs in the kernel does not look at the
btrees inode structure before reading the
inode buffers, which allows the remote authenticated user to read unrelated files, or to read and rewrite disk blocks that are bound to the active file at the time of the operation, but earlier were tied to an unbound file by accessing
NFS .
inode (inode) - data structure
btrees - data structure, search tree
NFS - Network File System Access Protocol
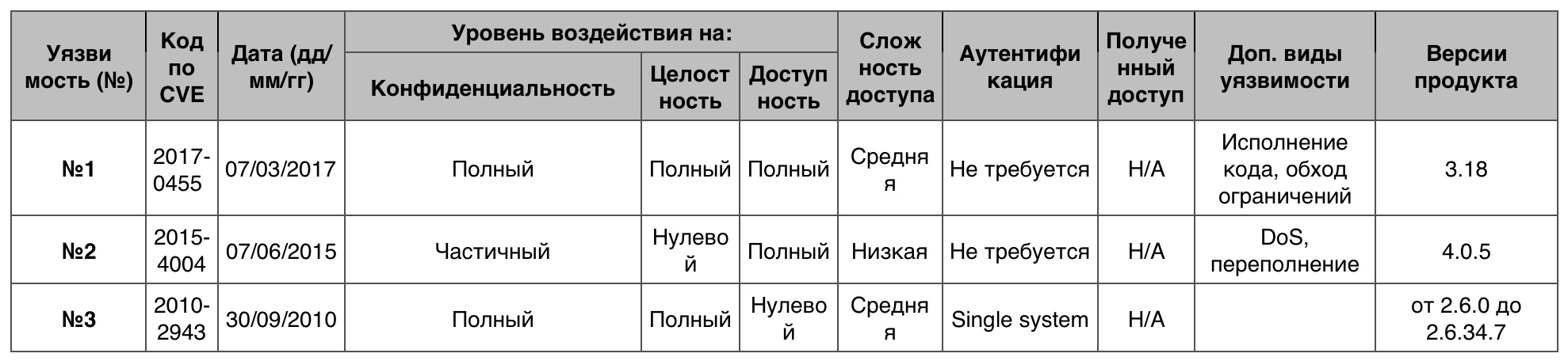 The Access to Information category vulnerability table in the Linux kernelPrivilege increase
The Access to Information category vulnerability table in the Linux kernelPrivilege increase3 vulnerabilities (10 points) of 250 total.
Vulnerability # 1The “capabilities” feature in Linux prior to version 2.2.16 allowed local users to obtain privileges by configuring capabilities to prevent the program from removing privileges
setuid .
setuid - set user ID at run time
Vulnerability # 2Multiple software overflows in a 32-bit emulator for AMD64 architectures allowed attackers to run DoS or get root privileges through unspecified vectors that activated copy_from_user function calls with incorrect length arguments.
Vulnerability # 3The use-after-free vulnerability in the kvm_ioctl_create_device function in virt / kvm / kvm_main.c allowed the host user to do DoS or get privileges through ioctl-created calls on the / dev / kvm device.
 Privilege Increase vulnerability table in the Linux kernelOverflow
Privilege Increase vulnerability table in the Linux kernelOverflowOf the 305 vulnerabilities, 17 scored 10 points.
Vulnerability # 1Possible software overflow in SMMU system call. Incorrect input validation in the ADSP SID2CB syscall can result in the hypervisor memory being overwritten.
Vulnerability # 2Buffer overflow in storage subsystem. Incorrect parameters as part of the response to RPMB commands can lead to a buffer overflow.
Vulnerability # 3In /drivers/isdn/i4l/isdn_net.c: the buffer controlled by the user is copied to the local buffer in a constant size using strcpy without checking the length, which can lead to a buffer overflow.
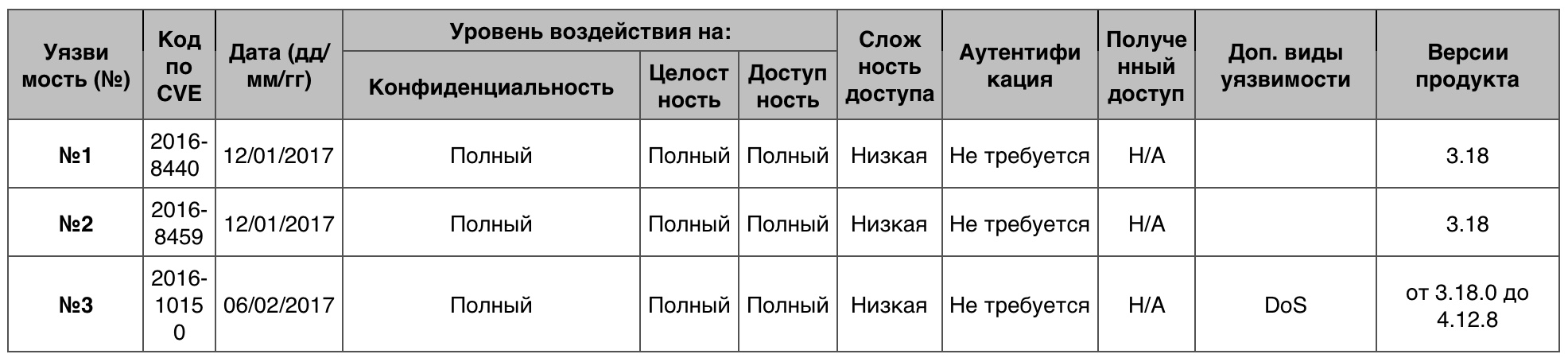 Vulnerability Table Overflow in the Linux kernel
Vulnerability Table Overflow in the Linux kernelAs can be seen from the data above, there are extremely few critical vulnerabilities. Most of them did not have a strong impact on system performance or data integrity.
3. Iphone Os
 Iphone Os
Iphone Os is an operating system for mobile devices (smartphones, tablets, etc.) from Apple. Since June 2010, simply referred to as iOS. First appearance - 2007. The total number of users worldwide is about 700 million people.
iOS for all the time of its existence has collected 1328 vulnerabilities, which is 624 less than Linux. However, the whole point is precisely in the period during which these statistics were collected. 1328 vulnerabilities in 10 years are much worse than 1952 in 19 years. And all again because of the popularity of this OS.
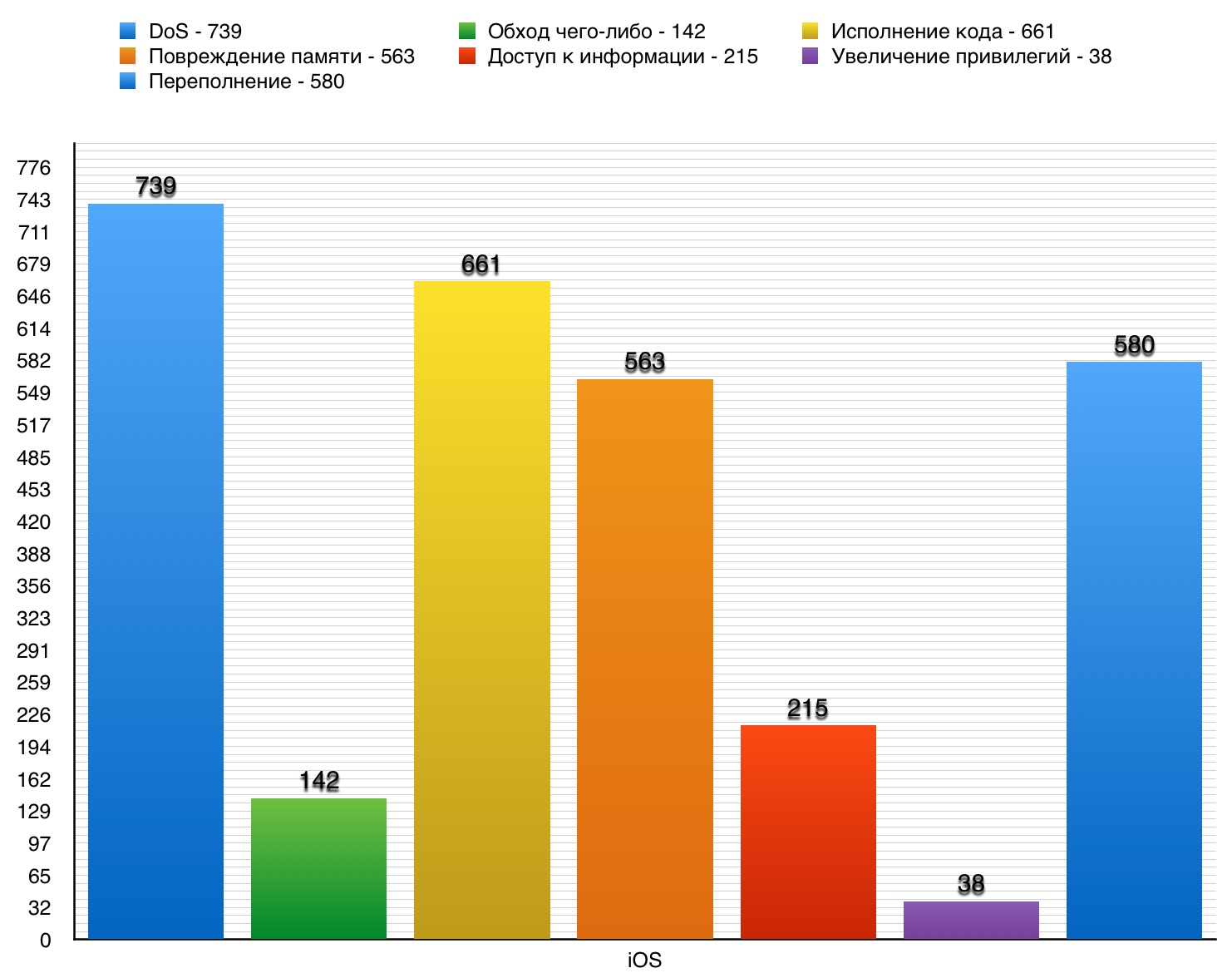 DoS
DoS11 vulnerabilities out of 739 scored 10 points.
Vulnerability # 1Up to version 10 iOS libxml2 allowed attackers to do DoS or execute code on the victim’s device by implementing the XML document they created.
Vulnerability # 2Audio on iOS devices below version 10 made it possible to organize DoS or execute code on an unidentified vector.
Vulnerability # 3On Broadcom BCM4355C0 Wi-Fi chips version 9.44.78.27.0.1.56 and other properly created
over-the-air frames could potentially provoke a heap of Wi-Fi firmware overflow and / or a stack overflow. This led to DoS.
over-the-air - cases of remote wireless control by an attacker of a mobile device.
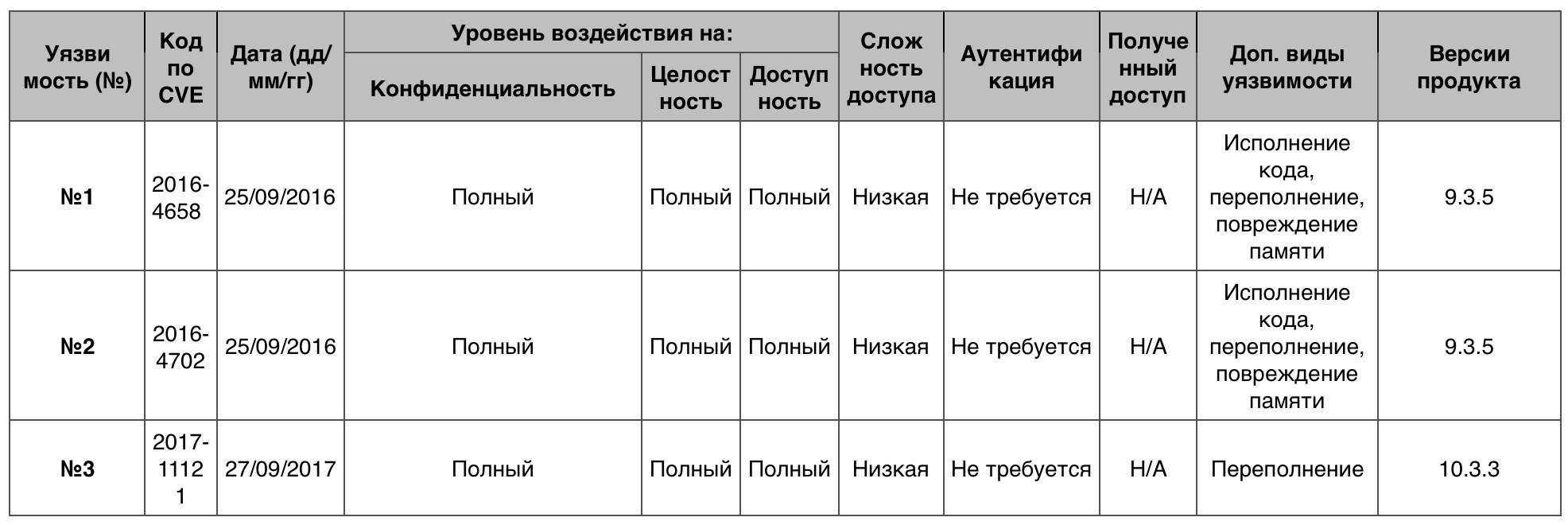 Table of vulnerabilities category "DoS" in iOSBypassing something
Table of vulnerabilities category "DoS" in iOSBypassing something1 vulnerability out of 142 scored 10 points.
Vulnerability # 1 (10)The kernel in iOS prior to version 8.1.3 does not apply the “read-only” attribute of the shared memory segment while using the user cache mode, which allows attackers to bypass the intended access restrictions through the created application.
Vulnerability # 2 (9.3)The iOS kernel prior to version 5.1 incorrectly handles debug system calls, which allows attackers to bypass the sandbox restrictions remotely.
Vulnerability # 3 (9.3)The iOS kernel before version 9.3 incorrectly restricts executive rights, which allows attackers to bypass the code signature protection mechanism through the created application.
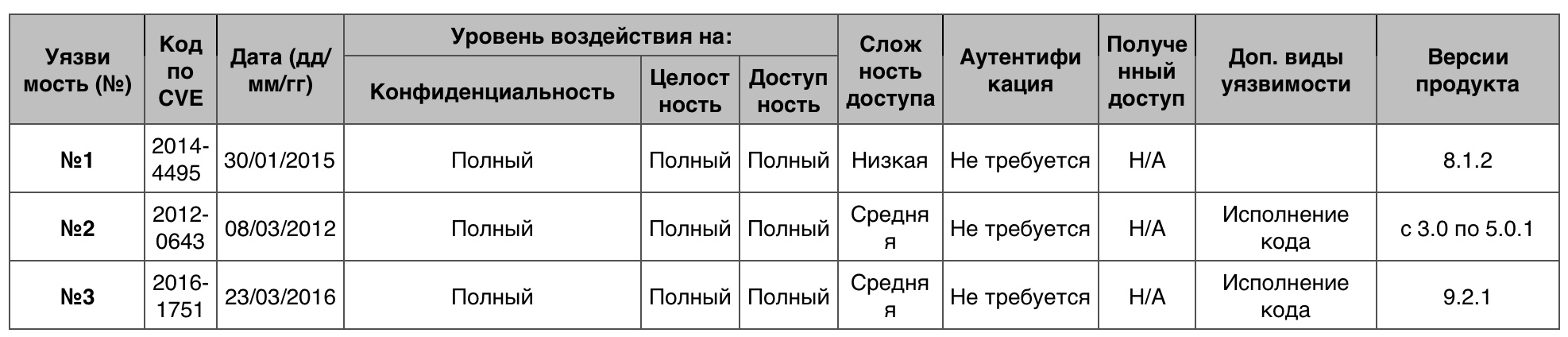 Vulnerability Table "Crawl" category in iOSCode execution
Vulnerability Table "Crawl" category in iOSCode execution17 out of 661 vulnerabilities - 10 points.
Vulnerability # 1Up to version 9.3, libxml2 in iOS allowed attackers to execute code on the victim’s device by embedding the XML document they created.
Vulnerability # 2Up to version 10 iOS libxml2 allowed attackers to do DoS or execute code on the victim’s device by implementing the XML document they created.
Vulnerability # 3Audio on iOS devices below version 10 made it possible to organize DoS or execute code on an unidentified vector.
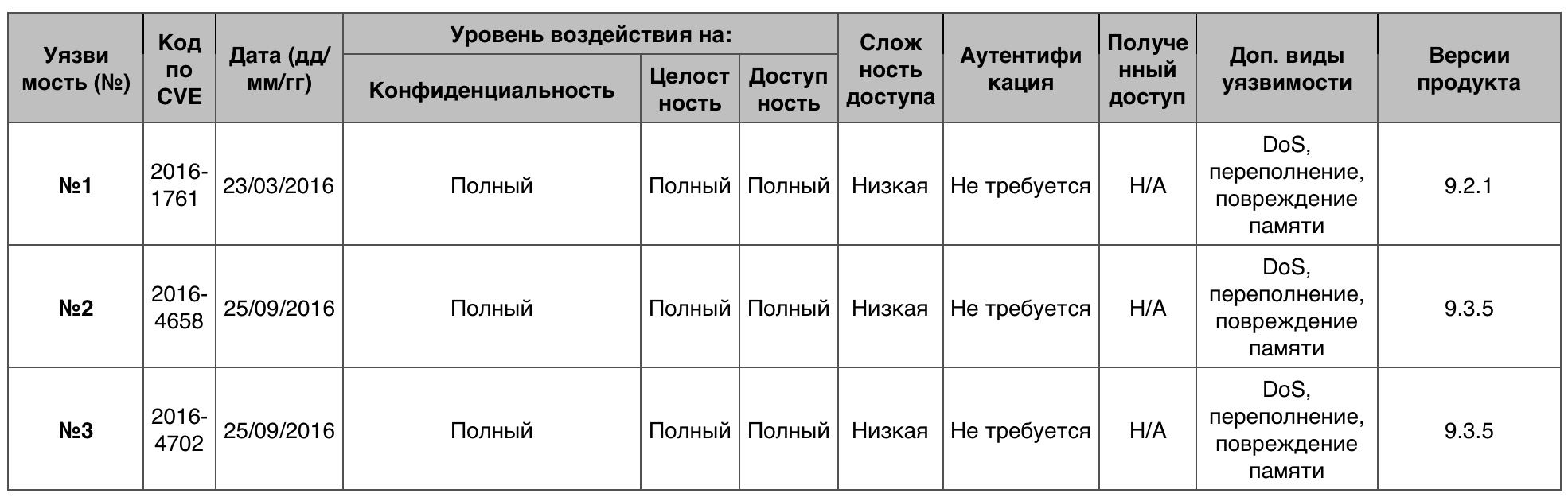 Code Execution Vulnerability Table for iOSMemory damage
Code Execution Vulnerability Table for iOSMemory damage6 out of 563 vulnerabilities scored 10 points.
Vulnerability # 1Up to version 9.3, libxml2 in iOS allowed attackers to damage the memory on the victim’s device by inserting the XML document they created.
Vulnerability # 2Up to version 10 of iOS libxml2 in iOS allowed attackers to damage the memory on the victim’s device by implementing the XML document they created.
Vulnerability # 3Audio on iOS devices below version 10 made it possible to damage memory or execute code using an unidentified vector.
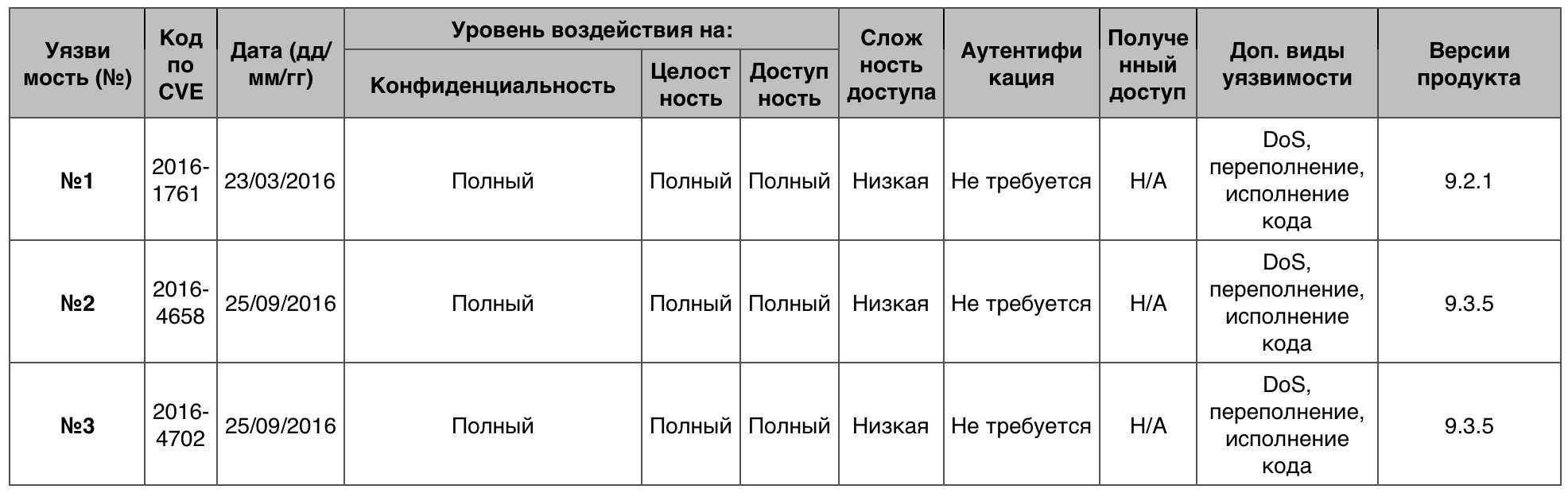 IOS Memory Vulnerability TableAccess to the information
IOS Memory Vulnerability TableAccess to the information, 10 .
№1 (7.5)iPhone OS 1.0-2.1 iPod touch 1.1-2.1 PPTP VPN , .
№2 (7.5)iOS 8.3 ICMP_REDIRECT , DoS , ICMP .
№3 (7.1)XSL WebKit iPhone OS 1.0-2.2.1 ( iPod touch 1.1-2.2.1) XML-,
DTD .
DTD — Document Type Definition — .
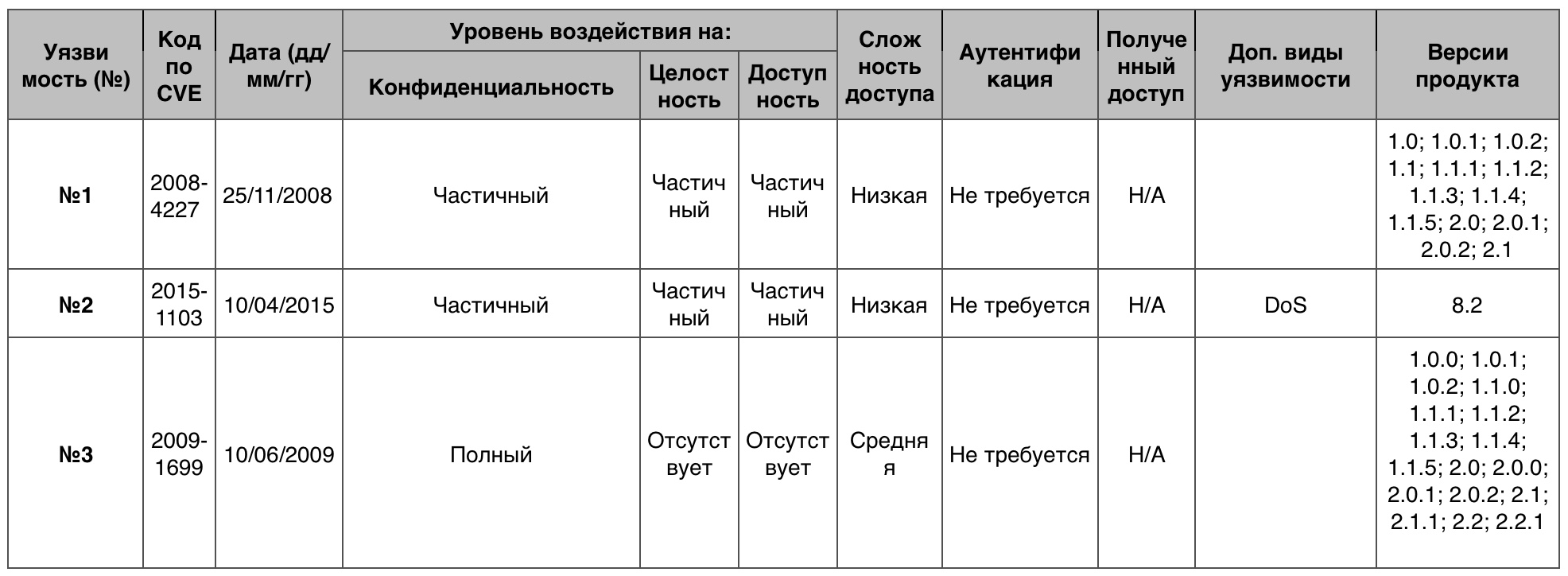 « » iOS
« » iOS1 38 10 .
№1 (10 )iOS 9 , DoS .
№2 (7.9)iOS 7-9 BlueBorne LEAP (Low Energy Audio Protocol) - -, , . -, LEAP, , Bluetooth . Bluetooth, Bluetooth .
№3 (7.2)iOS 4.2 , .
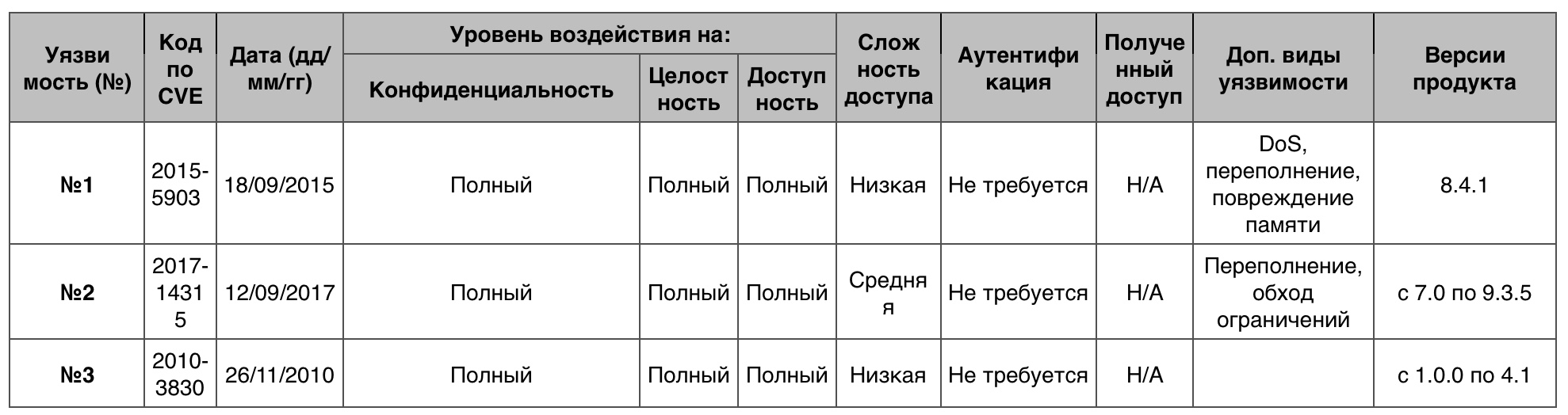 « » iOS
« » iOS14 580 10 .
№1NAS Qualcomm : iPhone 5 , iPad 4- , iPod touch 6- .
№2Wi-Fi Broadcom BCM4355C0 9.44.78.27.0.1.56 RRM Wi-Fi.
№3Wi-Fi Broadcom BCM4355C0 9.44.78.27.0.1.56 over-the-air Wi-Fi / .
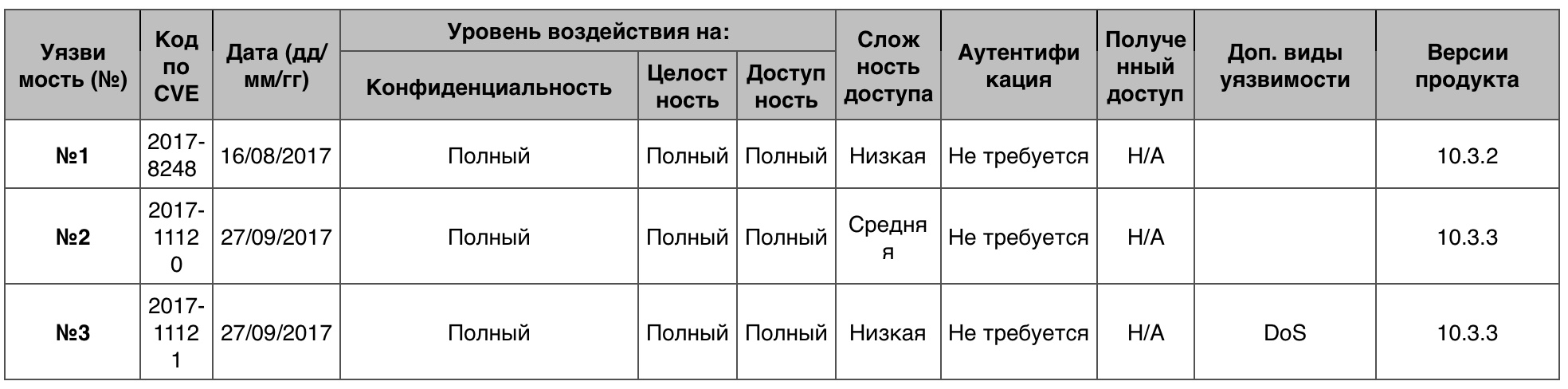 «» iOS
«» iOSAndroid , 10-. , . iOS App Store, . - . Android .
4. Windows 10
 Windows 10
Windows 10 — Microsoft, 2014 . 2017 500 .
Windows «» . Android, . 2017 Windows 10 255 , macOS — 236.
 DoS
DoS40 , DoS, , 10 , , .
№1 (9.3)atmfd.dll Adobe Type Manager DoS OpenType .
№2 (7.8)HTTP.sys DoS HTTP 2.0.
№3 (7.8), DoS.
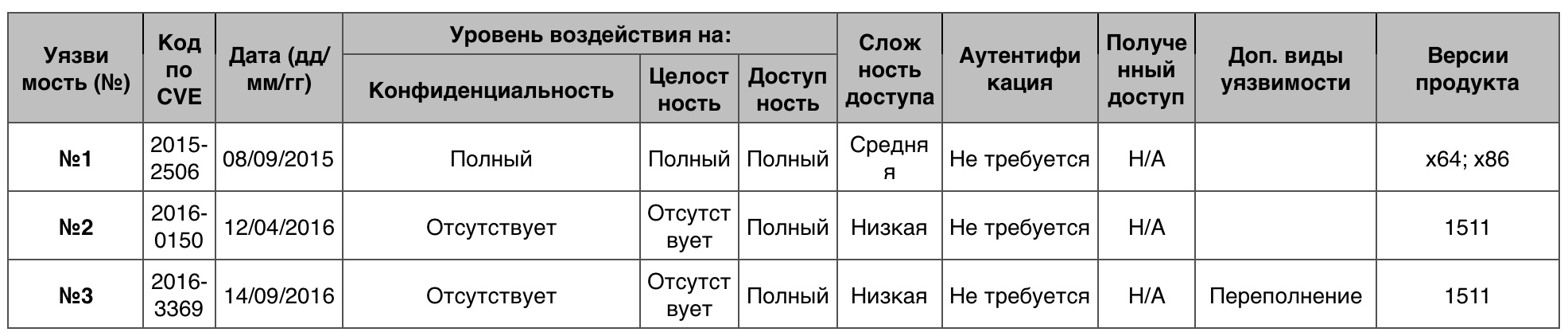 «DoS» Windows 10-
«DoS» Windows 10-42 , , , 10 , , .
№1 (9.3)RDP RDP .
№2 (7.2)Task Scheduler ( ) . .
№3 (7.2)CSRSS , .
CSRSS — -.
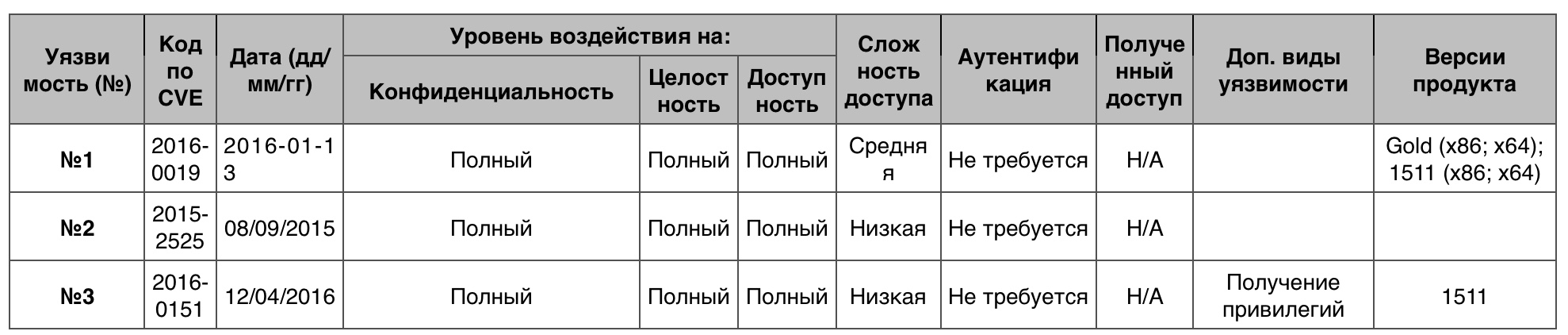 « -» Windows 10
« -» Windows 104 110 10 .
№1, Windows Search .
№2, Windows Search .
№3, DNS .
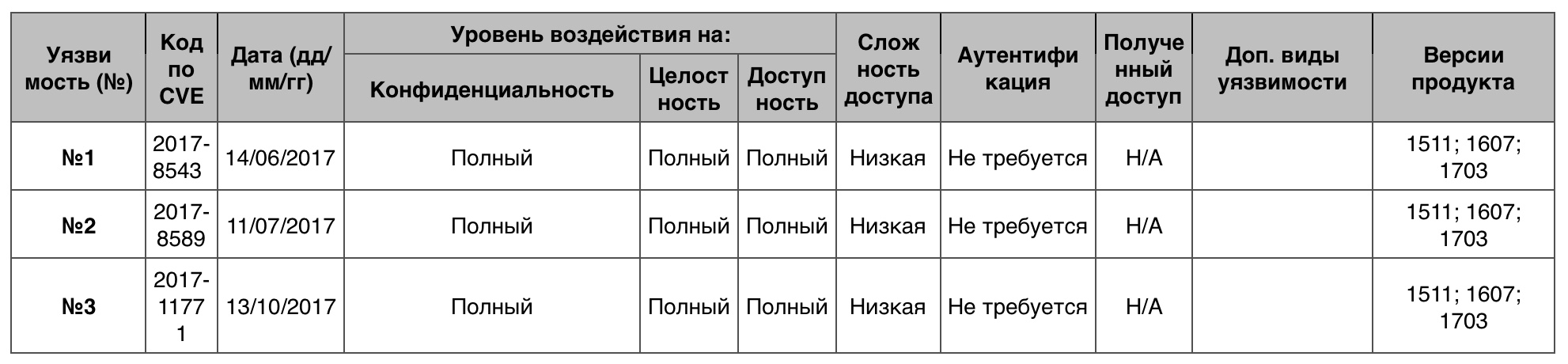 « » Windows 10
« » Windows 1014 , 10 . , .
№1 (9.3)The Imaging Component .
№2 (9.3)Animation Manager -.
№3 (9.3)Media Foundation -.
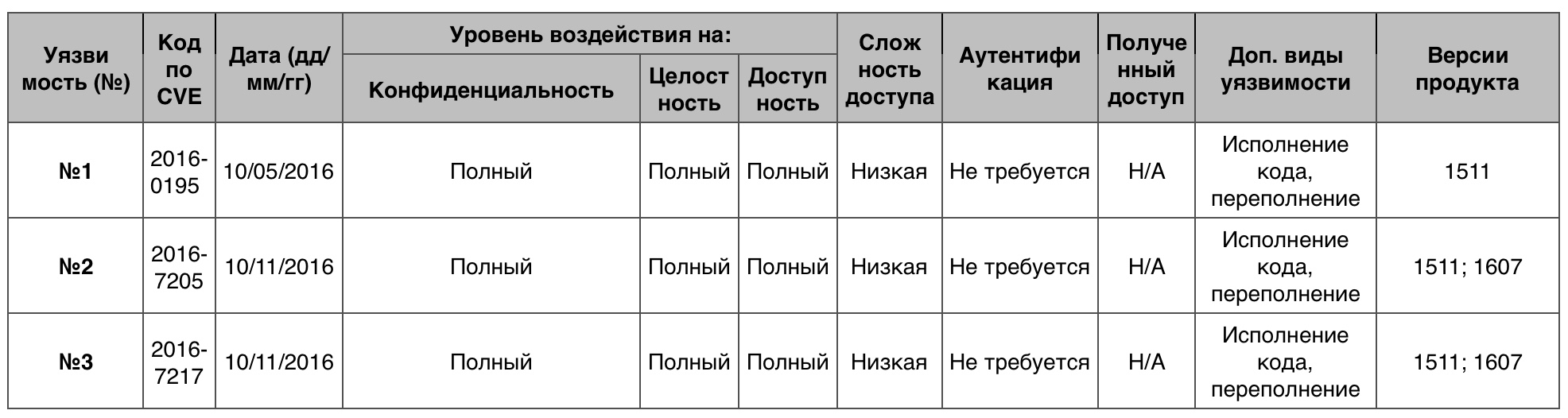 « » Windows 10
« » Windows 10140 . — 7.2.
№1 (7.2)DoS.
№2 (5.0)GDI (Graphics Device Interface) ASLR .
№3 (5.0)ActiveSyncProvider , Universal Outlook .
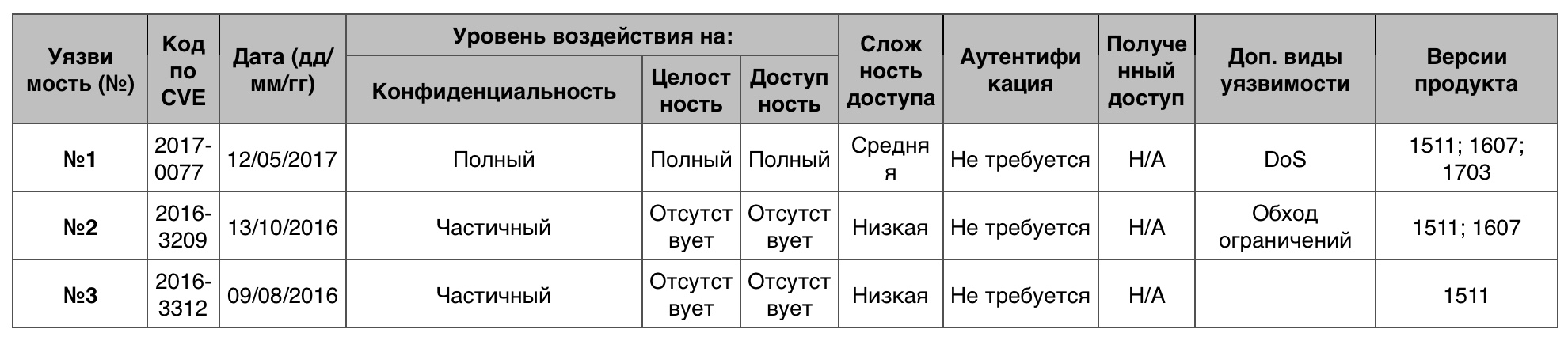 « » Windows 10
« » Windows 10127 2 10 .
№1 (10).
№2 (10).
№3 (9.3)CLFS .
CLFS — Common Log File System, , , , .
 « » Windows 10
« » Windows 109.3.
№1 ( 9.3)Windows Uniscribe .
№2 ( 9.3)Microsoft JET Database Engine , .
№3 ( 9.3)Microsoft JET Database Engine , .
 «» Windows 10
«» Windows 10Windows 10 . , , . , , , . « ». .
5. Windows Server 2016
 Windows Server 2016
Windows Server 2016 — Microsoft, 2016 . , . Windows 10, .
 DoS
DoS, DoS, , 29. 10 .
№1 (7.8)SMB DoS .
SMB — Server Block Message — , , , ..
№2 (7.2)API , , DoS .
№3 (7.2), DoS, . .
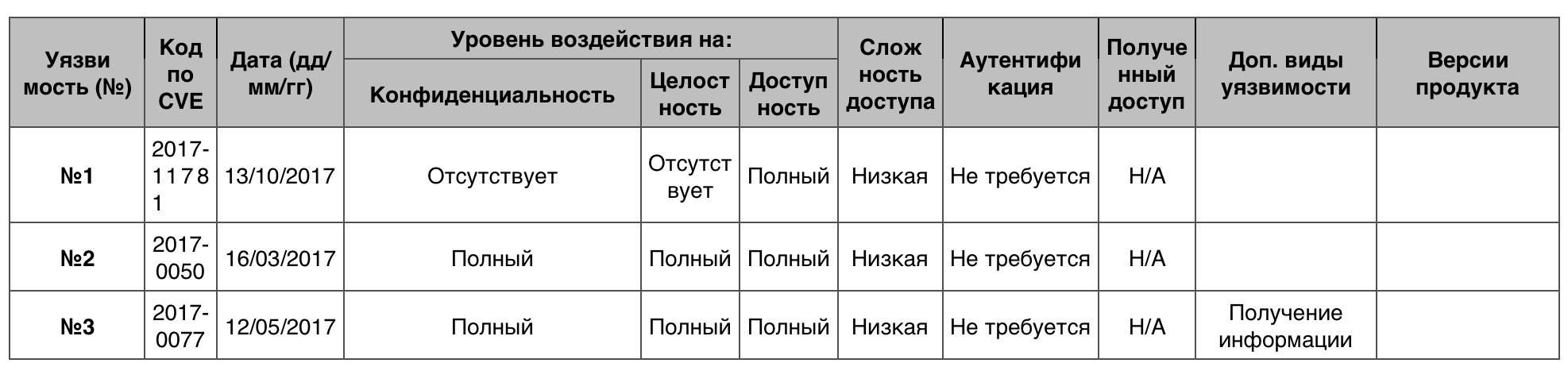 «DoS» Windows Server 2016-
«DoS» Windows Server 2016-15 — . — 6.0.
№1 (6.0), Kerberos SNAME «
».
Kerberos — , , .
«
» — Ticket —
№2 (5.0)Secure Boot boot .
№3 (4.6)VTL .
VTL — virtual trust level.
 « -» Windows Server 2016
« -» Windows Server 20163 53 10 .
№1, Windows Search .
№2, Windows Search .
№3, DNS .
 « » Windows Server 2016
« » Windows Server 20165 . — 9.3.
№1Animation Manager - .
№2Media Foundation - .
№3iSNS Server .
iSNS Server — Internet Storage Name Service — , ISCSI TCP/IP.
 « » Windows Server 2016
« » Windows Server 201697 10-, — 7.2.
№1 (7.2).
№2 (5.0)Windows Search , .
№3 (4.3)atmfd.dll Open Type -.
 « » Windows Server 2016
« » Windows Server 201636 ( 9.3).
№1 (9.3)CLFS .
CLFS — Common Log File System — , , , .
№2 (9.3)CLFS .
№3 (9.3)CLFS .
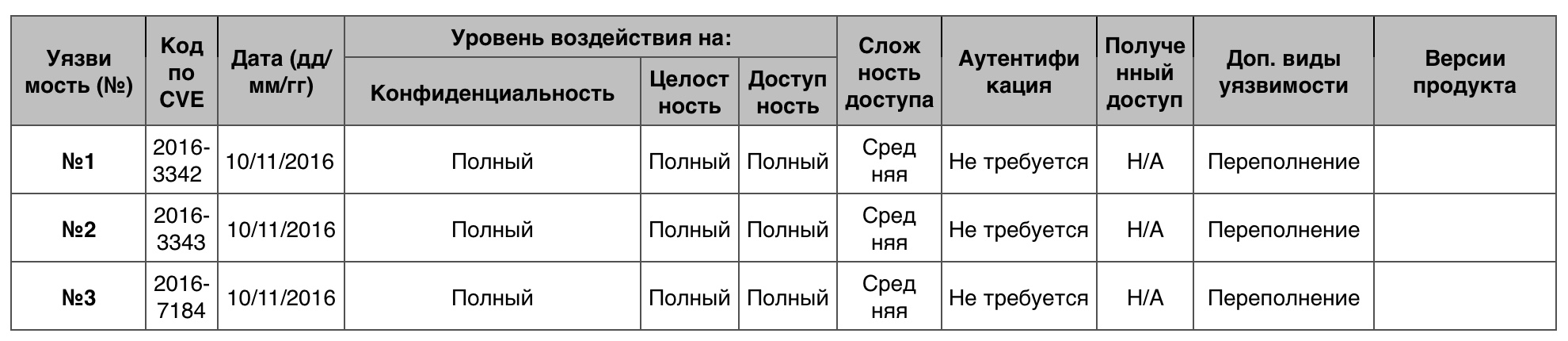 « » Windows Server 2016
« » Windows Server 201624 . 10 0 .
№1 (9.3)Uniscribe .
№2 (9.3)JET Database Engine , .
№3 (9.3)JET Database Engine , .
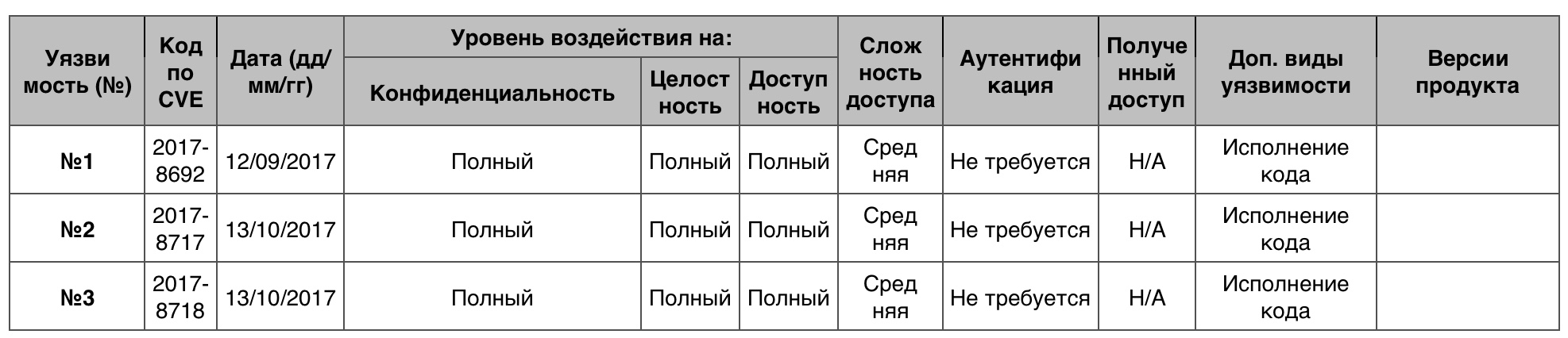 «» Windows Server 2016
«» Windows Server 2016Windows Server 2016 . , , . . , , . , , , , , , , .
. macOS Windows ( , ). , , . , , . . .
As advertising. These are not just virtual servers! This is a VPS (KVM) with dedicated drives, which can be no worse than dedicated servers, and in most cases - better!
We made VPS (KVM) with dedicated drives in the Netherlands and the USA (configurations from VPS (KVM) - E5-2650v4 (6 Cores) / 10GB DDR4 / 240GB SSD or 4TB HDD / 1Gbps 10TB available at a uniquely low price - from $ 29 / month , options are available with RAID1 and RAID10) , do not miss the chance to place an order for a new type of virtual server, where all resources belong to you, as on a dedicated one, and the price is much lower, with a much more productive hardware!
How to build the infrastructure of the building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny? Dell R730xd 2 times cheaper? Only we have
2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA!