
カスペルスキーセキュリティアナリストサミットの第4回年次会議が2月16日と17日にカンクンで開催されました(これはメキシコにあります)。 これはカスペルスキーにとって非常に重要なイベントです。そこでは、研究を共有し、情報セキュリティ業界の他の企業の同僚を招待しています。 Habréでの2つのプレゼンテーションはすでに議論されています。TheEquation APTとCarbanakの研究は多くの注目を集めました(ありがとう、
私は
喜んでコメント
を読んで、ここで質問に答える準備ができています)。 この投稿では、Carbanak、The Equationによる研究のプレゼンテーション、およびデザートファルコンと呼ばれる、これまで知られていなかった別のグループの活動に関する簡単なレポート。 3つすべて-Securelist Webサイトの研究者の詳細なレポートへのリンク。 まあ、いくつかの写真。 重要:ほぼすべてのパフォーマンスは、ビデオの後半で利用可能になります。別の投稿で投稿します。
カルバナック。 強盗。Securelist(rus)の
記事 。 技術的な詳細を含む
完全なレポート (eng)。
侵害のインジケータ (形式
。IOC )。
この投稿の議論では、ATMのハッキングに最も注意が払われました。 確かに、これはおそらくCarbanakの物語の最も共鳴的な部分です。コマンドを与えると、ATMはカード、PINコードなしでお金を発行し始めます。

これについて、Carbanakの作成者は穴を開けました。ATMが外部の干渉なしにこのように動作しないことは明らかです。 さらに調査したところ、ATMでのハッキングはお金を引き出す方法の1つにすぎませんでした。 攻撃者は自分の口座に資金を振り込み、残高を操作して、多くのセキュリティシステムがこれに気付かないようにすることができます。 国内の銀行システムを完全に制御することができなければ、そのような操作を開始することは不可能でした。 そのため、侵入後、ビデオ録画など、銀行のインフラストラクチャの配置に関する情報を収集するために、さまざまな方法が使用されました。

そして、攻撃は非常に単純に、またはむしろ習慣的に始まりました:
特にMicrosoft Office(CVE-2012-0158; CVE-2013-3906)およびMicrosoft Word(CVE-2014-1761)の脆弱性を悪用する感染した添付ファイル付きの手紙。10億ドルはどこから来たのですか?Carbanakの調査は、さまざまな国の法執行機関と緊密に協力して実施されました。 National Hi-Tech Crime UnitのPeter Zinnは、SASカンファレンスで作業のこの部分について話しました。

法執行機関からの情報により、Carbanakの被害者の合計数-約100の金融機関を推定することができました。 各犠牲者の死傷者は250万から1000万ドルの範囲であったことを考えると、Carbanakからの最大の損害はわずか10億ドルになります。
ボディシャツ感染の事実がすでに確認されており、感染したコンピューターを特定する必要がある調査中に興味深い話が起こりました。 これは、可能な限り迅速に行う必要がありました。まず、脅威をブロックし、次に調査用のサンプルを収集します。 このために簡単なスクリプトが作成されました。
方程式または「スタック、私はあなたの父親です」または帰属の難しさ。Securelistの
記事 。
Q&A (英語)。
Fannyモジュール(eng)の研究。
今年のすべてのSASゲストには、著者によるサイン入りのKim Zetter Stuxnetの
本が贈られまし
た 。 理解してもらうために:これは500ページのタルムードであり、Zetterによると、出版社は技術的な詳細を可能な限り減らすように要求しました。 The Equationについての本を書いたことがあれば、その大きさも同じです。 重要なポイント:現在、この操作の研究は初期段階にあります。 一般的な詳細のみを公開し、モジュールの1つを詳細に検討しました。 さらなる研究には、研究室と他の企業の両方で時間と労力が必要になります。 なんで? Equation APTの背後にいる人々は、10年以上、おそらく20年以上(C&Cサーバーの最初のドメインの登録日で数える場合)仕事をしています。
 SASの方程式について語ったKaspersky Labの研究者:Igor Sumenkov、Sergey Mineev、Vitaliy Kamlyuk、Kostin Raiu。Grzegorz Brz Brczyszczykiewicz
SASの方程式について語ったKaspersky Labの研究者:Igor Sumenkov、Sergey Mineev、Vitaliy Kamlyuk、Kostin Raiu。Grzegorz Brz BrczyszczykiewiczThe Equationの500人以上の犠牲者を確実に特定することができました。 自己破壊メカニズムが操作の悪意のあるモジュールに組み込まれているという事実を考慮すると、被害者の総数は数万に達する可能性があります。 その中には、政府機関、通信会社、航空機産業の代表者、石油およびガス部門などがあります。 そして、私たちの調査は、
Grzhegorzh Brzhezhishchichevichという名前の男が、CD-ROMドライブにフォトディスクを挿入した後、悪意のある攻撃の犠牲者であると疑い始めたときに始まりました。 このディスクは、彼が以前参加したヒューストンでの科学会議から彼に送られました。
もちろん、機密保持のためにこの人物の名前を変更しました。 このビデオのおかげで、そのようなエイリアスが選択された可能性があります。
方程式について今何を知っていますか? ドメイン登録とモジュールのコンパイルの日付から判断すると、キャンペーンは何十年もの間活発でした。 特に、最も古いモジュールはWindows 95/98をサポートしています。 情報を攻撃および収集するために、さまざまなモジュールとさまざまな感染方法が使用されました(たとえば、フォーラムの感染を通じて)。 Fannyとして知られるモジュールの1つは、アジアおよび中東の犠牲者に関する情報を収集するために使用され、2008年に作成され、2つのゼロデイ脆弱性を悪用しました。 同じ脆弱性が後でStuxnetで使用されました。 ここでのキーワードは「後で」です。この事実は、他のいくつかの事例と同様に、StuxnetとThe Equationの関係を示唆しています。
そして、このプラグインはおそらく最も興味深いものです。 ファイル名(nls_933w.dll)のみで知られているため、まれにしか使用されていないようで、例外的なケースでは、ハードドライブ(またはSSD)のファームウェアを変更できます。 なんで? まず、情報がドライブから完全に削除された場合でも、被害者のコンピューターの制御を取り戻すために。 第二に、信頼性が高く最も機密性の高いデータストレージ用です。 この手順の対象となる可能性がある12のドライブモデルの識別子は、プラグインコードで見つかりました。 ファームウェア分析の複雑さと、この場合のコードのエラーがハードドライブの完全な動作不能につながるという事実を考えると、このモジュールは、それを作成したグループの可能性がどれほど広いかを示します。
帰属これは非常に重要なポイントです。KasperskyLabは、Equation APTの背後にいる
人物についてはまだ
何も言えません。 このキャンペーンへの関与を合理的に非難したり、少なくとも手術が行われた地域や国を特定したりするのに十分な事実がありません。 現時点で他のすべては投機と投機であり、私たちはこれを行いません。 コード(方程式コードではなく、一般的に)で見つかったマルウェアの作成者の起源に関する明示的なヒントでさえ、研究者(または調査者)を間違った方向に導くために時々導入されるため、帰属は一般に非常に難しいタスクです。
2日間のSecurity Analyst Summitで、アトリビューションの複雑さについて何度も議論されています。 ジュニパーネットワークスのクリストファー・ホフによるプレゼンテーションでの投機的アプローチの逸話的な例:
でたらめ帰属ビンゴ。
 砂漠のファルコン:中東での新しいAPTキャンペーン
砂漠のファルコン:中東での新しいAPTキャンペーンSecurelistの
記事 。
詳細な調査 (eng、pdf)。

Dmitry BestuzhevのDesert Falconsキャンペーンに関する話で、攻撃者がいかに思慮深くソーシャルエンジニアリング手法を使用しているかに最も驚きました。 当然、彼らは電子メール経由で攻撃します。
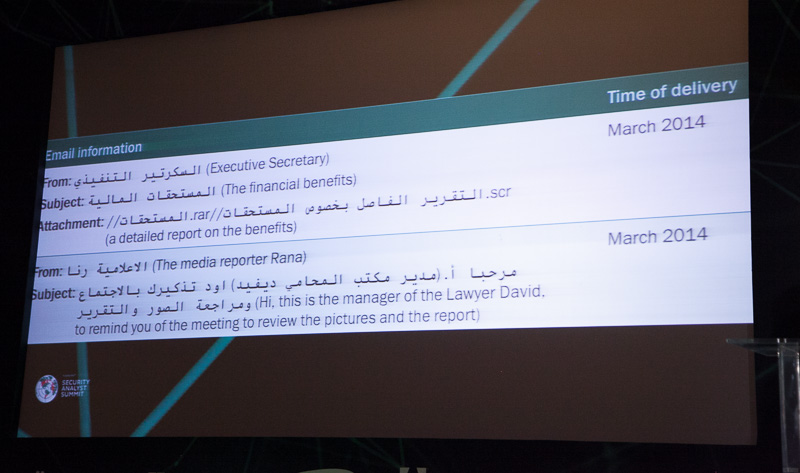
しかし、それだけではありません。 Facebookを使用します。 友人になり、プライベートでチャットし、
数か月の準備をし、感染したファイルへのリンクを最終的に送信するために信頼関係に入ります。 またはもっと簡単:彼らは影響力のある人々が他のユーザーから自分の壁に投稿を閉じないという事実を利用します。 潜在的な被害者にとって重要な重要なイベントに即座に対応し、電子メールでメッセージやメールを調整します。
デザートファルコンズキャンペーンの背後にいる人々は、犠牲者を非常によく知っています。 最も可能性が高いのは、彼ら自身が中東の国の1つに住んでいるためです。 これがまさにこの調査で重要なことです。新しいプレーヤーが、地元の風景をよく知っている(盗品を使用するのではなく)情報を攻撃および収集するための独自のツールを開発しています。 方程式とは異なり、操作は長く、現在は非アクティブであり、「砂漠のハヤブサ」は比較的最近(2011年以降)作業を開始し、現在では最適な形になっています。 結果:データを盗むためにコンピューターやAndroidベースのモバイルデバイスにマルウェアが感染し、データによると、
3,000人以上の犠牲者からの
100万を超えるファイルとドキュメントが攻撃者の手に渡りました。
さらにブログで。 Security Analyst Summitでのプレゼンテーションの結果に基づいて、犯罪目的で、特に暗号ロッカーで合法的なソフトウェアを使用する機能など、いくつかのトピックを準備しています。 カスペルスキーデイリーのこの壮大な
ライブブログで、SASでのほぼすべてのパフォーマンスの引用やソーシャルネットワークでの視聴者の最も興味深い発言を知ることができます。