セキュリティジャーナルの監査は、同僚がサーバーまたはActiveDirectoryに少なくともある程度アクセスできる従業員のほぼすべてのアクティビティを監視するのに役立ちました。
このトピックには多くのコードがありますが、それが皆さんの役に立つことを願っています。
最初のステップは、追跡する必要があるイベントのリストを決定することでした。 テキストの量を減らすために、イベントIDに応じてその説明を提供するプロシージャを作成しました。
Function DefineReason ($Id){ switch ($Id){ 4741{ Return " "} 4742{ Return " " } 4743{ Return " "} 4727{ Return " "} 4728{ Return " "} 4729{ Return " "} 4730{ Return " "} 4731{ Return " "} 4732{ Return " "} 4733{ Return " "} 4734{ Return " "} 4735{ Return " "} 4737{ Return " "} 4743{ Return " "} 4754{ Return " " } 4755{ Return " "} 4756{ Return " "} 4757{ Return " "} 4758{ Return " "} 4764{ Return " "} 4720{ Return " "} 4722{ Return " "} 4724{ Return " "} 4725{ Return " "} 4726{ Return " "} 4738{ Return " "} 4740{ Return " "} 4767{ Return " "} 4780{ Return " , "} 4781{ Return " "} 4794{ Return " "} 5376{ Return " : "} 5377{ Return " : "} 4825{ Return "e , RDP"} 1102{ Return " Security"} } }
次に、アクセスマスクによって追跡されるイベントを記述する必要がありました。
これで、何をフォローしたいかがわかりました。 監査スクリプトを開発する次の手順は、XML形式のセキュリティログを取得することです。イベントが多数ある場合、行ごとの処理にはかなり長い時間がかかるためです。
ジャーナルからイベントを取得するには、次のコマンドのいずれかを使用できます。各コマンドにはそれぞれ利点と欠点があります。
1. Get-LogEventセキュリティ
利点:
-イベントプロパティへのクイックアクセス。
-イベントプロパティにアクセスするための前処理は必要ありません。
短所:
-Windows / System32 / winevt / security.evtxのパスに沿って保存されているシステムセキュリティログからのみアクセスできます。
-タグのコンテンツの長時間処理。 処理は、特殊文字を除去した行ごとの分離によって行われます。
2. Get-WinEvent –path“ D:/”
利点:
-高速ジャーナル処理。
-任意の雑誌へのアクセス。 主なことは、完全なパスを規定することです。
短所:
-受信したジャーナルを処理するには前処理が必要です。
Try { $Events = Get-WinEvent -FilterHashTable $MyFilter } Catch {"No events were found in $Log"; Continue} ForEach ($Raw_Event in $Events) { Try{ $EventXML = [xml]$Raw_Event.ToXML() } Catch {Write-Host "Unable to convert an event to XML"} $Event = @{} ForEach ($object in $EventXML.Event.EventData.Data) { $Event.Add($object.name,$object.'#text') } $Event.Add("ID",$Raw_Event.ID) $Event.Add("TimeCreated",$Raw_Event.TimeCreated)
ジャーナルにアクセスした後の次のステップは、ジャーナルから必要なイベントを引き出して、適切な決定を下すことです。 ほとんどの場合、これは情報メッセージをメールに送信するか、別のファイルにログインします。
おそらくインターフェイスソリューションを使用して、情報を抽出するパラメーターを設定します。 入力パラメーターのあるダイアログボックス。
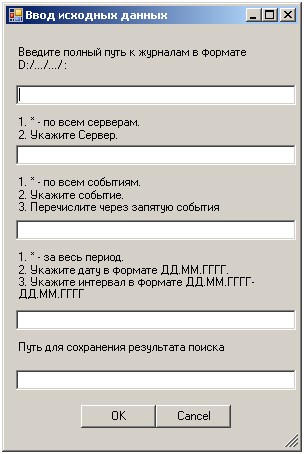
1.最初のパラメーターは、ログが特定のディレクトリに定期的にエクスポートされることを前提としています。 ログが1つしかない場合は、ログを保存するための標準ディレクトリ「C:\ Windows \ System32 \ winevt \ Logs」が設定されます。
2. 2番目のパラメーターは、ログを検索するサーバーを決定します。 サーバーが1つの場合は、「*」を入力します。
3. 3番目のパラメーターは非常に明確です:*-日付が設定されている場合(2015年11月30日など)、この日付を検索します。 期間の検索は、ダッシュ(11/01/2015-11/30/2015)で開始日と終了日を入力することにより実行されます。
4.「D:\ log.log」など、作業結果を保存するパスを指定します。 以下は、スクリプトのインターフェイスを構築できるコードです。
$objForm = New-Object System.Windows.Forms.Form $objForm.Text = " " $objForm.Size = New-Object System.Drawing.Size(300,450) $objForm.StartPosition = "CenterScreen"
入力されたデータを取得します。
日付フィールドに「-」記号がある場合、この記号が正しく入力されていないと、間隔が入力されます-問題。 記号「-」で区切りを実行し、範囲の開始日と終了日を決定します。
if ($DateEventsmode -match "-"){ $x = $DateEventsmode.split("-") $StartDate = $x[0] $EndDate = $x[1] $StartDate = [DateTime]::parse($StartDate) $StartDate $EndDate = [DateTime]::parse($EndDate) $EndDate }
入力フィールドに「-」も「*」もない場合、特定の日付が入力されます。
if ($DateEventsmode -notmatch "-" -and $DateEventsmode -ne "*"){ $StartDate1 = [DateTime]::parse($DateEventsmode) }
1.すべてのサーバー、すべてのイベント、期間全体を検索します。
if ($FindServerMode -eq "*" -and $DateEventsmode -eq "*" -and $TypeEventsMode -eq "*" -and $Log_Path -ne ""){ Write-host " 1" $ALL_LOGS = Get-ChildItem -Path $Log_Path -recurse| Where {$_.Extension -eq ".evtx"} | Sort LastWriteTime $ALL_LOGS foreach ($Log in $ALL_LOGS){ $LogFile = "Audit EventLog Security" +"`n" ($Log).FullName $MyFilter = @{Path=($Log).FullName} $i=0 Try {$Events = Get-WinEvent -FilterHashTable $MyFilter} Catch {"No events were found in $Log"; Continue} ForEach ($Raw_Event in $Events){ Try{$EventXML = [xml]$Raw_Event.ToXML()} Catch {Write-Host "Unable to convert an event to XML"} $Event = @{} ForEach ($object in $EventXML.Event.EventData.Data) { $Event.Add($object.name,$object.'#text') } $Event.Add("ID",$Raw_Event.ID) $Event.Add("TimeCreated",$Raw_Event.TimeCreated) $LogFile+= "EventID: " + $Raw_Event.ID +"`n" $LogFile+= "Target User Name: " + $Event.TargetUserName +"`n" $LogFile+= "Target Domain Name: " + $Event.TargetDomainName +"`n" $LogFile+= "Status: " + $Event.Status +"`n" $LogFile+= "TimeGenerated: " + $Event.TimeCreated +"`n" $LogFile+= "Workstation Name: " + $Event.WorkstationName +"`n" $LogFile+= "IpAddress: " + $Event.IpAddress +"`n" $LogFile+= "Computer: " + [xml]$Raw_Event.ToXML().Event.System.Computer +"`n" $Reason = DefineReason -Id $Raw_Event.ID $AccessM = DefineReasonByAccessMask -AccessMask $Event.Status $LogFile+= "Reason(RU): " + $Reason + " "+ $AccessM +"`n" $LogFile+= "Reason(SYS): " + $Event.Message +"`n" $LogFile+= "----------------------------------------------------------------`n" $i++ } } }
2.期間全体について、イベントフィルターですべてのサーバーを検索します。
if ($FindServerMode -eq "*" -and $DateEventsmode -eq "*" -and $TypeEventsMode -ne "*" -and $Log_Path -ne ""){ Write-host " 2" $ALL_LOGS = Get-ChildItem -Path $Log_Path | Where {$_.Extension -eq ".evtx"} | Sort LastWriteTime $ALL_LOGS foreach ($Log in $ALL_LOGS){ $LogFile = "Audit EventLog Security" +"`n" ($Log).FullName $MyFilter = @{Path=($Log).FullName;ID=$TypeEventsMode} Try {$Events = Get-WinEvent -FilterHashTable $MyFilter} Catch {"No events were found in $Log"; Continue} ForEach ($Raw_Event in $Events){ Try{$EventXML = [xml]$Raw_Event.ToXML()} Catch {Write-Host "Unable to convert an event to XML"} $Event = @{} ForEach ($object in $EventXML.Event.EventData.Data) { $Event.Add($object.name,$object.'#text') } $Event.Add("ID",$Raw_Event.ID) $Event.Add("TimeCreated",$Raw_Event.TimeCreated) $LogFile+= "EventID: " + $Event.ID +"`n" $LogFile+= "Target User Name: " + $Event.TargetUserName +"`n" $LogFile+= "Target Domain Name: " + $Event.TargetDomainName +"`n" $LogFile+= "Status: " + $Event.Status +"`n" $LogFile+= "TimeGenerated: " + $Event.TimeCreated +"`n" $LogFile+= "Workstation Name: " + $Event.WorkstationName +"`n" $LogFile+= "IpAddress: " + $Event.IpAddress +"`n" $LogFile+= "Computer: " + [xml]$Raw_Event.ToXML().Event.System.Computer +"`n" $Reason = DefineReason -Id $Raw_Event.ID $AccessM = DefineReasonByAccessMask -AccessMask $Event.Status $LogFile+= "Reason(RU): " + $Reason + " "+ $AccessM +"`n" $LogFile+= "Reason(SYS): " + $Event.Message +"`n" $LogFile+= "----------------------------------------------------------------`n" } } }
3.すべてのサーバー、すべてのイベントで、範囲を検索します。
if ($FindServerMode -eq "*" -and $DateEventsmode -match "-" -and $TypeEventsMode -eq "*" -and $Log_Path -ne ""){ Write-host " 3" $ALL_LOGS = Get-ChildItem -Path $Log_Path -Recurse| Where {$_.Extension -eq ".evtx" } | Sort LastWriteTime $ALL_LOGS foreach ($Log in $ALL_LOGS){ $LogFile = "Audit EventLog Security" +"`n" ($Log).FullName $StartDate $EndDate $MyFilter = @{Path=($Log).FullName} Try {$Events = Get-WinEvent -FilterHashTable $MyFilter} Catch {"No events were found in $Log"; Continue} ForEach ($Raw_Event in $Events){ Try{$EventXML = [xml]$Raw_Event.ToXML()} Catch {Write-Host "Unable to convert an event to XML"} $Event = @{} ForEach ($object in $EventXML.Event.EventData.Data) { $Event.Add($object.name,$object.'#text') } $Event.Add("ID",$Raw_Event.ID) $Event.Add("TimeCreated",$Raw_Event.TimeCreated) $Event.TimeCreated if ($Event.TimeCreated -gt $StartDate -and $Event.TimeCreated -lt $EndDate){ $LogFile+= "EventID: " + $Raw_Event.ID +"`n" $LogFile+= "Target User Name: " + $Event.TargetUserName +"`n" $LogFile+= "Target Domain Name: " + $Event.TargetDomainName +"`n" $LogFile+= "Status: " + $Event.Status +"`n" $LogFile+= "TimeGenerated: " + $Event.TimeCreated +"`n" $LogFile+= "Workstation Name: " + $Event.WorkstationName +"`n" $LogFile+= "IpAddress: " + $Event.IpAddress +"`n" $LogFile+= "Computer: " + [xml]$Raw_Event.ToXML().Event.System.Computer +"`n" $Reason = DefineReason -Id $Raw_Event.ID $AccessM = DefineReasonByAccessMask -AccessMask $Event.Status $LogFile+= "Reason(RU): " + $Reason + " "+ $AccessM +"`n" $LogFile+= "Reason(SYS): " + $Event.Message +"`n" $LogFile+= "----------------------------------------------------------------`n" } } } }
4.すべてのサーバー、すべてのイベントで、特定の日付を検索します。
if ($FindServerMode -eq "*" -and $DateEventsmode -notmatch "-" -and $DateEventsmode -ne "*" -and $TypeEventsMode -eq "*" -and $Log_Path -ne ""){ Write-host " 5" $ALL_LOGS = Get-ChildItem -Path $Log_Path -Recurse| Where {$_.Extension -eq ".evtx" -and $StartDate1 -ne "null" } | Sort LastWriteTime $ALL_LOGS foreach ($Log in $ALL_LOGS){ $LogFile = "Audit EventLog Security" +"`n" ($Log).FullName $Log.LastWriteTime $StartDate $EndDate $MyFilter = @{Path=($Log).FullName} Try {$Events = Get-WinEvent -FilterHashTable $MyFilter} Catch {"No events were found in $Log"; Continue} ForEach ($Raw_Event in $Events){ Try{$EventXML = [xml]$Raw_Event.ToXML()} Catch {Write-Host "Unable to convert an event to XML"} $Event = @{} ForEach ($object in $EventXML.Event.EventData.Data) { $Event.Add($object.name,$object.'#text') } $Event.Add("ID",$Raw_Event.ID) $Event.Add("TimeCreated",$Raw_Event.TimeCreated) if ($Event.TimeCreated.Day -eq $StartDate1.Day -and $Event.TimeCreated.Month -eq $StartDate1.Month -and $Event.TimeCreated.Year -eq $StartDate1.Year){ $LogFile+= "EventID: " + $Raw_Event.ID +"`n" $LogFile+= "Target User Name: " + $Event.TargetUserName +"`n" $LogFile+= "Target Domain Name: " + $Event.TargetDomainName +"`n" $LogFile+= "Status: " + $Event.Status +"`n" $LogFile+= "TimeGenerated: " + $Event.TimeCreated +"`n" $LogFile+= "Workstation Name: " + $Event.WorkstationName +"`n" $LogFile+= "IpAddress: " + $Event.IpAddress +"`n" $LogFile+= "Computer: " + [xml]$Raw_Event.ToXML().Event.System.Computer +"`n" $Reason = DefineReason -Id $Raw_Event.ID $AccessM = DefineReasonByAccessMask -AccessMask $Event.Status $LogFile+= "Reason(RU): " + $Reason + " "+ $AccessM +"`n" $LogFile+= "Reason(SYS): " + $Event.Message +"`n" $LogFile+= "----------------------------------------------------------------`n" } } } }
5.特定の期間、イベントフィルターによってすべてのサーバーを検索します。
if ($FindServerMode -eq "*" -and $DateEventsmode -match "-" -and $DateEventsmode -ne "*" -and $TypeEventsMode -ne "*" -and $Log_Path -ne ""){ Write-host " 4" $ALL_LOGS = Get-ChildItem -Path $Log_Path -Recurse| Where {$_.Extension -eq ".evtx" -and $StartDate1 -ne ""} | Sort LastWriteTime $ALL_LOGS foreach ($Log in $ALL_LOGS){ $LogFile = "Audit EventLog Security" +"`n" ($Log).FullName $Log.LastWriteTime $StartDate $EndDate $MyFilter = @{Path=($Log).FullName;ID=$TypeEventsMode} Try {$Events = Get-WinEvent -FilterHashTable $MyFilter} Catch {"No events were found in $Log"; Continue} ForEach ($Raw_Event in $Events){ Try{$EventXML = [xml]$Raw_Event.ToXML()} Catch {Write-Host "Unable to convert an event to XML"} $Event = @{} ForEach ($object in $EventXML.Event.EventData.Data) { $Event.Add($object.name,$object.'#text') } $Event.Add("ID",$Raw_Event.ID) $Event.Add("TimeCreated",$Raw_Event.TimeCreated) if ($Event.TimeCreated.Day -eq $StartDate1.Day -and $Event.TimeCreated.Month -eq $StartDate1.Month -and $Event.TimeCreated.Year -eq $StartDate1.Year){ $LogFile+= "EventID: " + $Raw_Event.ID +"`n" $LogFile+= "Target User Name: " + $Event.TargetUserName +"`n" $LogFile+= "Target Domain Name: " + $Event.TargetDomainName +"`n" $LogFile+= "Status: " + $Event.Status +"`n" $LogFile+= "TimeGenerated: " + $Event.TimeCreated +"`n" $LogFile+= "Workstation Name: " + $Event.WorkstationName +"`n" $LogFile+= "IpAddress: " + $Event.IpAddress +"`n" $LogFile+= "Computer: " + [xml]$Raw_Event.ToXML().Event.System.Computer +"`n" $Reason = DefineReason -Id $Raw_Event.ID $AccessM = DefineReasonByAccessMask -AccessMask $Event.Status $LogFile+= "Reason(RU): " + $Reason + " "+ $AccessM +"`n" $LogFile+= "Reason(SYS): " + $Event.Message +"`n" $LogFile+= "----------------------------------------------------------------`n" } } } }
6.特定の日付について、イベントフィルターによってすべてのサーバーを検索します。
if ($FindServerMode -eq "*" -and $TypeEventsMode -ne "*" -and $DateEventsmode -notmatch "-" -and $DateEventsmode -ne "*" -and $Log_Path -ne "") { Write-host " 6" $ALL_LOGS = Get-ChildItem -Path $Log_Path -Recurse| Where {$_.Extension -eq ".evtx" -and $StartDate1 -ne "" } | Sort LastWriteTime $ALL_LOGS foreach ($Log in $ALL_LOGS){ $LogFile = "Audit EventLog Security" +"`n" ($Log).FullName $Log.LastWriteTime $StartDate $EndDate $MyFilter = @{Path=($Log).FullName;ID=$TypeEventsMode} Try {$Events = Get-WinEvent -FilterHashTable $MyFilter} Catch {"No events were found in $Log"; Continue} ForEach ($Raw_Event in $Events){ Try{$EventXML = [xml]$Raw_Event.ToXML()} Catch {Write-Host "Unable to convert an event to XML"} $Event = @{} ForEach ($object in $EventXML.Event.EventData.Data) { $Event.Add($object.name,$object.'#text') } $Event.Add("ID",$Raw_Event.ID) $Event.Add("TimeCreated",$Raw_Event.TimeCreated) if ($Event.TimeCreated.Day -eq $StartDate1.Day -and $Event.TimeCreated.Month -eq $StartDate1.Month -and $Event.TimeCreated.Year -eq $StartDate1.Year){ $LogFile+= "EventID: " + $Raw_Event.ID +"`n" $LogFile+= "Target User Name: " + $Event.TargetUserName +"`n" $LogFile+= "Target Domain Name: " + $Event.TargetDomainName +"`n" $LogFile+= "Status: " + $Event.Status +"`n" $LogFile+= "TimeGenerated: " + $Event.TimeCreated +"`n" $LogFile+= "Workstation Name: " + $Event.WorkstationName +"`n" $LogFile+= "IpAddress: " + $Event.IpAddress +"`n" $LogFile+= "Computer: " + [xml]$Raw_Event.ToXML().Event.System.Computer +"`n" $Reason = DefineReason -Id $Raw_Event.ID $AccessM = DefineReasonByAccessMask -AccessMask $Event.Status $LogFile+= "Reason(RU): " + $Reason + " "+ $AccessM +"`n" $LogFile+= "Reason(SYS): " + $Event.Message +"`n" $LogFile+= "----------------------------------------------------------------`n" } } } }
7.期間全体のすべてのイベントを特定のサーバーで検索します。
if ($FindServerMode -ne "*" -and $DateEventsmode -eq "*" -and $TypeEventsMode -eq "*" -and $Log_Path -ne ""){ Write-host " 7" $ALL_LOGS = Get-ChildItem -Path $Log_Path -Recurse| Where {$_.Extension -eq ".evtx" -and $_.FullName -match $FindServerMode} | Sort LastWriteTime $ALL_LOGS foreach ($Log in $ALL_LOGS){ $LogFile = "Audit EventLog Security" +"`n" ($Log).FullName $MyFilter = @{Path=($Log).FullName} Try {$Events = Get-WinEvent -FilterHashTable $MyFilter} Catch {"No events were found in $Log"; Continue} ForEach ($Raw_Event in $Events){ Try{$EventXML = [xml]$Raw_Event.ToXML()} Catch {Write-Host "Unable to convert an event to XML"} $Event = @{} ForEach ($object in $EventXML.Event.EventData.Data) { $Event.Add($object.name,$object.'#text') } $Event.Add("ID",$Raw_Event.ID) $Event.Add("TimeCreated",$Raw_Event.TimeCreated) $LogFile+= "EventID: " + $Raw_Event.ID +"`n" $LogFile+= "Target User Name: " + $Event.TargetUserName +"`n" $LogFile+= "Target Domain Name: " + $Event.TargetDomainName +"`n" $LogFile+= "Status: " + $Event.Status +"`n" $LogFile+= "TimeGenerated: " + $Event.TimeCreated +"`n" $LogFile+= "Workstation Name: " + $Event.WorkstationName +"`n" $LogFile+= "IpAddress: " + $Event.IpAddress +"`n" $LogFile+= "Computer: " + [xml]$Raw_Event.ToXML().Event.System.Computer +"`n" $Reason = DefineReason -Id $Raw_Event.ID $AccessM = DefineReasonByAccessMask -AccessMask $Event.Status $LogFile+= "Reason(RU): " + $Reason + " "+ $AccessM +"`n" $LogFile+= "Reason(SYS): " + $Event.Message +"`n" $LogFile+= "----------------------------------------------------------------`n" } } }
8.期間全体について、イベントフィルターによって特定のサーバーで検索します。
if ($FindServerMode -ne "*" -and $DateEventsmode -eq "*" -and $TypeEventsMode -ne "*" -and $Log_Path -ne ""){ Write-host " 8" $ALL_LOGS = Get-ChildItem -Path $Log_Path -Recurse| Where {$_.Extension -eq ".evtx" -and $_.FullName -match $FindServerMode} | Sort LastWriteTime $ALL_LOGS foreach ($Log in $ALL_LOGS){ $LogFile = "Audit EventLog Security" +"`n" ($Log).FullName $MyFilter = @{Path=($Log).FullName;ID=$TypeEventsMode} Try {$Events = Get-WinEvent -FilterHashTable $MyFilter} Catch {"No events were found in $Log"; Continue} ForEach ($Raw_Event in $Events){ Try{$EventXML = [xml]$Raw_Event.ToXML()} Catch {Write-Host "Unable to convert an event to XML"} $Event = @{} ForEach ($object in $EventXML.Event.EventData.Data) { $Event.Add($object.name,$object.'#text') } $Event.Add("ID",$Raw_Event.ID) $Event.Add("TimeCreated",$Raw_Event.TimeCreated) $LogFile+= "EventID: " + $Event.ID +"`n" $LogFile+= "Target User Name: " + $Event.TargetUserName +"`n" $LogFile+= "Target Domain Name: " + $Event.TargetDomainName +"`n" $LogFile+= "Status: " + $Event.Status +"`n" $LogFile+= "TimeGenerated: " + $Event.TimeCreated +"`n" $LogFile+= "Workstation Name: " + $Event.WorkstationName +"`n" $LogFile+= "IpAddress: " + $Event.IpAddress +"`n" $LogFile+= "Computer: " + [xml]$Raw_Event.ToXML().Event.System.Computer +"`n" $Reason = DefineReason -Id $Raw_Event.ID $AccessM = DefineReasonByAccessMask -AccessMask $Event.Status $LogFile+= "Reason(RU): " + $Reason + " "+ $AccessM +"`n" $LogFile+= "Reason(SYS): " + $Event.Message +"`n" $LogFile+= "----------------------------------------------------------------`n" } } }
9.特定のサーバーで、すべてのイベントについて、期間を検索します。
if ($FindServerMode -ne "*"-and $DateEventsmode -match "-" -and $TypeEventsMode -eq "*" -and $Log_Path -ne ""){ Write-host " 9" $ALL_LOGS = Get-ChildItem -Path $Log_Path -Recurse| Where {$_.Extension -eq ".evtx" -and $_.FullName -match $FindServerMode -and $StartDate -ne "null" -and $EndDate -ne "null"} | Sort LastWriteTime $ALL_LOGS foreach ($Log in $ALL_LOGS){ $LogFile = "Audit EventLog Security" +"`n" ($Log).FullName $Log.LastWriteTime $StartDate $EndDate $MyFilter = @{Path=($Log).FullName} Try {$Events = Get-WinEvent -FilterHashTable $MyFilter} Catch {"No events were found in $Log"; Continue} ForEach ($Raw_Event in $Events){ Try{$EventXML = [xml]$Raw_Event.ToXML()} Catch {Write-Host "Unable to convert an event to XML"} $Event = @{} ForEach ($object in $EventXML.Event.EventData.Data) { $Event.Add($object.name,$object.'#text') } $Event.Add("ID",$Raw_Event.ID) $Event.Add("TimeCreated",$Raw_Event.TimeCreated) if ($Event.TimeCreated -gt $StartDate -and $Event.TimeCreated -lt $EndDate){ $LogFile+= "EventID: " + $Raw_Event.ID +"`n" $LogFile+= "Target User Name: " + $Event.TargetUserName +"`n" $LogFile+= "Target Domain Name: " + $Event.TargetDomainName +"`n" $LogFile+= "Status: " + $Event.Status +"`n" $LogFile+= "TimeGenerated: " + $Event.TimeCreated +"`n" $LogFile+= "Workstation Name: " + $Event.WorkstationName +"`n" $LogFile+= "IpAddress: " + $Event.IpAddress +"`n" $LogFile+= "Computer: " + [xml]$Raw_Event.ToXML().Event.System.Computer +"`n" $Reason = DefineReason -Id $Raw_Event.ID $AccessM = DefineReasonByAccessMask -AccessMask $Event.Status $LogFile+= "Reason(RU): " + $Reason + " "+ $AccessM +"`n" $LogFile+= "Reason(SYS): " + $Event.Message +"`n" $LogFile+= "----------------------------------------------------------------`n" } } } }
10.特定のサーバーで、イベントフィルターを使用して期間を検索します。
if ($FindServerMode -ne "*" -and $DateEventsmode -match "-" -and $DateEventsmode -ne "*" -and $TypeEventsMode -ne "*" -and $Log_Path -ne ""){ Write-host " 10" $ALL_LOGS = Get-ChildItem -Path $Log_Path | Where {$_.Extension -eq ".evtx" -and $_.FullName -match $FindServerMode -and $StartDate -ne "null" -and $EndDate -ne "null"} | Sort LastWriteTime $ALL_LOGS foreach ($Log in $ALL_LOGS){ $LogFile = "Audit EventLog Security" +"`n" ($Log).FullName $Log.LastWriteTime $StartDate $EndDate $MyFilter = @{Path=($Log).FullName;ID=$TypeEventsMode} Try {$Events = Get-WinEvent -FilterHashTable $MyFilter} Catch {"No events were found in $Log"; Continue} ForEach ($Raw_Event in $Events){ Try{$EventXML = [xml]$Raw_Event.ToXML()} Catch {Write-Host "Unable to convert an event to XML"} $Event = @{} ForEach ($object in $EventXML.Event.EventData.Data) { $Event.Add($object.name,$object.'#text') } $Event.Add("ID",$Raw_Event.ID) $Event.Add("TimeCreated",$Raw_Event.TimeCreated) if ($Event.TimeCreated -gt $StartDate -and $Event.TimeCreated -lt $EndDate){ $LogFile+= "EventID: " + $Raw_Event.ID +"`n" $LogFile+= "Target User Name: " + $Event.TargetUserName +"`n" $LogFile+= "Target Domain Name: " + $Event.TargetDomainName +"`n" $LogFile+= "Status: " + $Event.Status +"`n" $LogFile+= "TimeGenerated: " + $Event.TimeCreated +"`n" $LogFile+= "Workstation Name: " + $Event.WorkstationName +"`n" $LogFile+= "IpAddress: " + $Event.IpAddress +"`n" $LogFile+= "Computer: " + [xml]$Raw_Event.ToXML().Event.System.Computer +"`n" $Reason = DefineReason -Id $Raw_Event.ID $AccessM = DefineReasonByAccessMask -AccessMask $Event.Status $LogFile+= "Reason(RU): " + $Reason + " "+ $AccessM +"`n" $LogFile+= "Reason(SYS): " + $Event.Message +"`n" $LogFile+= "----------------------------------------------------------------`n" } } } }
11.特定の日付の特定のサーバー、すべてのイベントを検索します。
if ($FindServerMode -ne "*" -and $DateEventsmode -notmatch "-" -and $DateEventsmode -ne "*" -and $TypeEventsMode -eq "*" -and $Log_Path -ne ""){ Write-host " 11" $ALL_LOGS = Get-ChildItem -Path $Log_Path -Recurse| Where {$_.Extension -eq ".evtx" -and $StartDate1 -ne "null" } | Sort LastWriteTime $ALL_LOGS foreach ($Log in $ALL_LOGS){ $LogFile = "Audit EventLog Security" +"`n" ($Log).FullName $Log.LastWriteTime $StartDate $EndDate $MyFilter = @{Path=($Log).FullName} Try {$Events = Get-WinEvent -FilterHashTable $MyFilter} Catch {"No events were found in $Log"; Continue} ForEach ($Raw_Event in $Events){ Try{$EventXML = [xml]$Raw_Event.ToXML()} Catch {Write-Host "Unable to convert an event to XML"} $Event = @{} ForEach ($object in $EventXML.Event.EventData.Data) { $Event.Add($object.name,$object.'#text') } $Event.Add("ID",$Raw_Event.ID) $Event.Add("TimeCreated",$Raw_Event.TimeCreated) if ($Event.TimeCreated.Day -eq $StartDate1.Day -and $Event.TimeCreated.Month -eq $StartDate1.Month -and $Event.TimeCreated.Year -eq $StartDate1.Year){ $LogFile+= "EventID: " + $Raw_Event.ID +"`n" $LogFile+= "Target User Name: " + $Event.TargetUserName +"`n" $LogFile+= "Target Domain Name: " + $Event.TargetDomainName +"`n" $LogFile+= "Status: " + $Event.Status +"`n" $LogFile+= "TimeGenerated: " + $Event.TimeCreated +"`n" $LogFile+= "Workstation Name: " + $Event.WorkstationName +"`n" $LogFile+= "IpAddress: " + $Event.IpAddress +"`n" $LogFile+= "Computer: " + [xml]$Raw_Event.ToXML().Event.System.Computer +"`n" $Reason = DefineReason -Id $Raw_Event.ID $AccessM = DefineReasonByAccessMask -AccessMask $Event.Status $LogFile+= "Reason(RU): " + $Reason + " "+ $AccessM +"`n" $LogFile+= "Reason(SYS): " + $Event.Message +"`n" $LogFile+= "----------------------------------------------------------------`n" } } } }
12.特定の日付の特定のサーバー、イベントフィルターを検索します。
if ($FindServerMode -ne "*" -and $TypeEventsMode -ne "*" -and $DateEventsmode -notmatch "-" -and $DateEventsmode -ne "*" -and $Log_Path -ne ""){ Write-host " 12" $ALL_LOGS = Get-ChildItem -Path $Log_Path -Recurse| Where {$_.Extension -eq ".evtx" -and $StartDate1 -ne "null" } | Sort LastWriteTime $ALL_LOGS foreach ($Log in $ALL_LOGS){ $LogFile = "Audit EventLog Security" +"`n" ($Log).FullName $Log.LastWriteTime $StartDate $EndDate $MyFilter = @{Path=($Log).FullName;ID=$TypeEventsMode} Try {$Events = Get-WinEvent -FilterHashTable $MyFilter} Catch {"No events were found in $Log"; Continue} ForEach ($Raw_Event in $Events){ Try{$EventXML = [xml]$Raw_Event.ToXML()} Catch {Write-Host "Unable to convert an event to XML"} $Event = @{} ForEach ($object in $EventXML.Event.Message) { $Event.Add($object.name,$object.'#text') } $Event.Add("ID",$Raw_Event.ID) $Event.Add("TimeCreated",$Raw_Event.TimeCreated) $Event if ($Event.TimeCreated.Day -eq $StartDate1.Day -and $Event.TimeCreated.Month -eq $StartDate1.Month -and $Event.TimeCreated.Year -eq $StartDate1.Year){ $LogFile+= "EventID: " + $Raw_Event.ID +"`n" $LogFile+= "Target User Name: " + $Event.TargetUserName +"`n" $LogFile+= "Target Domain Name: " + $Event.TargetDomainName +"`n" $LogFile+= "Status: " + $Event.Status +"`n" $LogFile+= "TimeGenerated: " + $Event.TimeCreated +"`n" $LogFile+= "Workstation Name: " + $Event.WorkstationName +"`n" $LogFile+= "IpAddress: " + $Event.IpAddress +"`n" $LogFile+= "Computer: " + [xml]$Raw_Event.ToXML().Event.System.Computer +"`n" $Reason = DefineReason -Id $Raw_Event.ID $AccessM = DefineReasonByAccessMask -AccessMask $Event.Status $LogFile+= "Reason(RU): " + $Reason + " "+ $AccessM +"`n" $LogFile+= "Reason(SYS): " + $Event.Message +"`n" $LogFile+= "----------------------------------------------------------------`n" } } } }
月末(期間は管理者によって個別に設定されます)に、セキュリティログがサーバー名とアーカイブの日付と共にストレージサーバーにアーカイブされます。イベントを検索するためのすべてのオプションを説明した後。結果をファイルに保存する必要があります。ファイルは、ユーザーが最後のフィールドに登録したパスです。パスが指定されている場合、結果はファイルに保存されます。スクリプトを実行した後、ファイルは自動的に起動されます。結果を保存するパスが指定されていない場合、ログは「log.log」という名前で作業ディレクトリに保存されます。 if ($SaveResult -ne ""){ $LogFile | Out-File $SaveResult -Encoding utf8 Invoke-Item $SaveResult $Event2= @{} $Event = @{} $Log_Path="" } else{ $LogFile | Out-File ".\log.log" -Encoding utf8 Write-Host $LogFile $Event2= @{} $Event = @{} $Log_Path="" }
ご清聴ありがとうございました。
スクリプトの作成中、「PowerShell and Security Auditing」という記事は、著者のおかげで非常に役立つことがわかりました。