楽しい時間、Habrauser!
パスワードレス認証のアイデアを共有したいと思います。 最近、私は認証センターのサイトを登って、面白いことに出会いました。 CAは、パスワードの代わりに証明書認証を使用します。 これは会社にとっては便利で、単純なユーザーがうろついている通常のインターネットサイトではなく、AD(サイトの管理センター)に入るのがいいと思います。
ここでは、このような社内の認証構造を提案します。
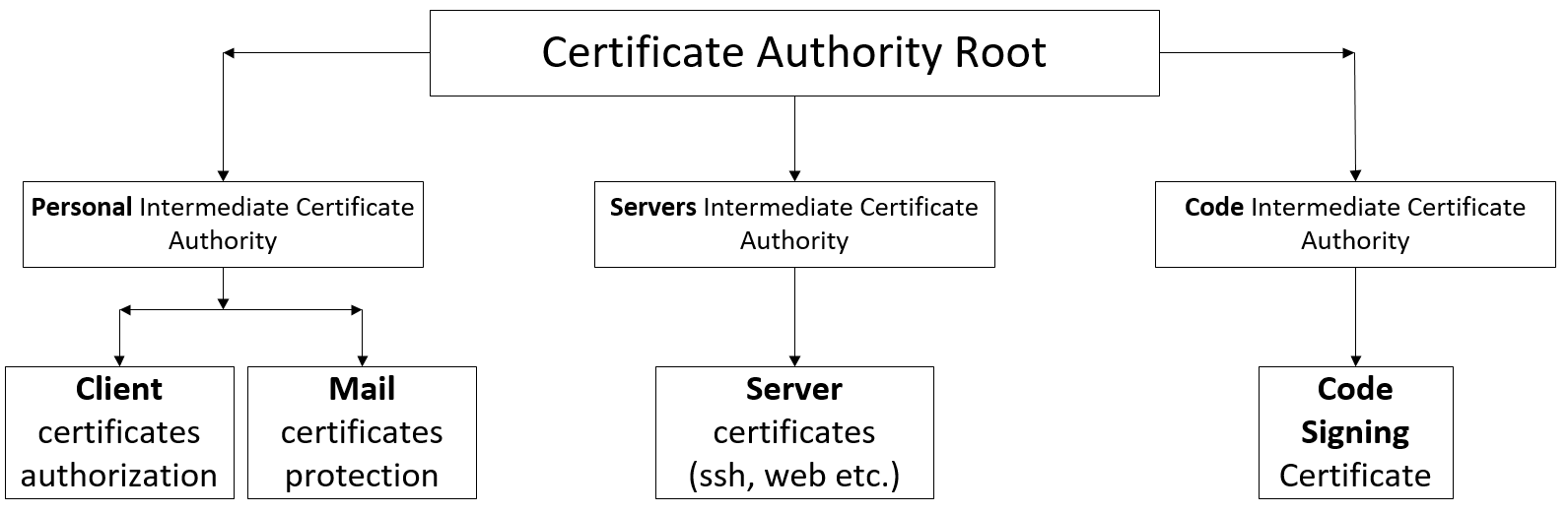
ドメイン名CertService.infoでCertService会社に任意に電話します。異なる部門があることも知っていますが、それらには触れません。 次に、ディレクトリ構造を理解し、opensslの構成について説明します。
CAサーバー上のディレクトリ構造
メインディレクトリは/ root / caです。 しかし、彼女の中にはすでに次のようなものがあります。
- RootCA- ルート証明書ディレクトリ
- 構成-OpenSSLの構成
- PersonIntermediateCA- ユーザー証明書の中間証明書
- ServerIntermediateCA- サーバー証明書の中間証明書
- CodeIntermediateCA- コード署名証明書の中間証明書
- これらのディレクトリには独自のディレクトリがあり、それらを見てください: (/ root / ca / {RootCA、PersonIntermediateCA、ServerIntermediateCA、CodeIntermediateCA})
- certs- 証明書のディレクトリ
- crl- 失効した証明書のディレクトリ
- csr- このディレクトリは中間証明書専用です(証明書作成要求)
- private(chmod 400)- 秘密鍵のディレクトリ
- index.txt- 証明書テキストデータベースファイル
- serial- 次の証明書のシリアル番号
- crlnumber- 次の証明書失効のシリアル番号
- 必要なディレクトリとファイルについて少し理解しました。 それでは、CAのOpenSSL構成の一部の記述に移りましょう。
OpenSSLの構成セクション
[ca]
[ca]セクションは必須です。 気にせず、デフォルトで独自のセクションが必要であることを伝えます。
[ ca ] default_ca = CA_default
[CA_default]
[CA_default]セクションで、デフォルト値を設定します。 最初に、メインディレクトリのパスを書きます
[ CA_default ] # , # ( ) dir = /root/ca/RootCA certs = $dir/certs new_certs_dir = $certs private = $dir/certs crl_dir = $dir/crl serial = $dir/serial database = $dir/index.txt RANDFILE = $dir/private/.rand
- 時間を節約するために、dirは専ら変数です。 ここでは、構成の対象となるCAのメインディレクトリまでを示します。
- certs-この変数は証明書用です。フォルダーを指定します。
- new_certs_dir-証明書(OpenSSLの異なるバージョンの証明書の異なる変数)に似ているため、両方を指定します。
- private-この変数には、プライベートディレクトリの場所を渡します。ディレクトリの説明では、ここにプライベートキーを保存すると既に述べています。
- crl_dir-すでに述べたように、失効した証明書のディレクトリへのパスがあります。
- serial-シリアルファイルを指定します。
- データベース-テキストデータベース、index.txt。
- RANDFILEは、ランダムデータ用のランダムファイルです。
先に進み、特定のパラメーターを指定します
# , , # ( - ) private_key = $private/RootCA.key.pem certificate = $certs/RootCA.cert.pem # crlnumber = $dir/crlnumber crl = $crl_dir/RootCA.crl.pem crl_extensions = crl_ext default_crl_days = 30 # default_md = sha256 name_opt = ca_default cert_opt = ca_default default_days = 365 preserve = no policy = policy_root
- private_keyとcertificate-秘密鍵と証明書のパスとファイル名をそれぞれ指定します。 これらのオプションは、証明書に署名するときに使用されます。 現時点では、ルート証明書が指定されています(中間証明書に署名します)。
- crlnumber-彼らが言うように、失効のためのシリアル番号を持つファイルへのパス。
- crl-取り消された証明書のファイル(ステートメントが正しいかどうか不明)
- crl_extensions-crlのときに呼び出される拡張子。
- default_crl_days-新しいCRLまでの日数。
- default_md-ハッシュアルゴリズム。
- name_optおよびcert_opt-検証済み証明書に関する情報の出力および出力形式を担当します。
- default_days-証明書が有効になる日数。
- preserve-最終証明書を、フィールドの順序とルート(または中間)に一致させます。
- policy-証明書に署名するためのポリシー。
政策
ポリシー-異なる構成では、異なる値を指定します。 それらのいくつかがあります:policy_root、policy_intermediate_person、policy_intermediate_server、policy_intermediate_code。
policy_root-ルート証明書の構成に含まれ、中間証明書に署名するための厳格なルールが設定されます。
policy_intermediate-ルールのこのセクションは中間構成にあり、署名ルールはそれほど厳密ではありません。
パラメータ:
- match-必須の完了、ルートCAとの完全一致
- 指定-必須の完了。必ずしもルートCAとの一致ではない
- オプション-オプションのフィールド
注で言及したポリシーを記述します
[ policy_root ] countryName = match stateOrProvinceName = match organizationName = match organizationalUnitName = supplied commonName = supplied emailAddress = optional subjectAltName = optional [ policy_intermediate_person ] countryName = optional stateOrProvinceName = optional localityName = optional organizationName = match organizationalUnitName = optional commonName = supplied emailAddress = supplied subjectAltName = optional [ policy_intermediate_code ] countryName = optional stateOrProvinceName = optional localityName = optional organizationName = match organizationalUnitName = optional commonName = supplied emailAddress = optional subjectAltName = optional [ policy_intermediate_server ] countryName = optional stateOrProvinceName = optional localityName = optional organizationName = match organizationalUnitName = optional commonName = supplied emailAddress = supplied subjectAltName = supplied
ここでは、停止しません。 すべてはすでに以前に描かれています。 そして、私は少し後でフィールドについて話します。
[必須]
[req]セクションのパラメーターは、証明書または証明書署名要求を作成するときに使用されます。
[ req ] default_bits = 2048 distinguished_name = req_distinguished_name string_mask = utf8only default_md = sha256 # -x509. x509_extensions = root_ca
ここで何が言えますか:
- default_bits-デフォルトのRSAキーサイズ。
- 識別名-このパラメーターは、証明書のパラメーターがリストされているセクションを呼び出します。
- string_mask-証明書に含まれるテキストのエンコーディング。
- default_md-同じハッシュアルゴリズム。
- x509_extensions-x509パラメータが指定されたときに使用されるセクションです。
[req_distinguished_name]
先ほど述べたように、ここでは証明書に必要なフィールドをリストします。
[ req_distinguished_name ] countryName = Country Name (2 letter code) (C) countryName_min = 2 countryName_max = 2 countryName_default = RU stateOrProvinceName = State or Province Name (S) stateOrProvinceName_default = Krasnoyarskiy kray localityName = Locality Name (L) localityName_default = Norilsk 0.organizationName = Organization Name (O) 0.organizationName_default = CertService organizationalUnitName = Organizational Unit Name (OU) organizationalUnitName_default = CertService. IT-Department. commonName = Common Name (CN) #commonName_default = CertService.info emailAddress = Email Address emailAddress_max = 60 #emailAddress_default = support@CertService.info subjectAltName = Alternative DNS names (comma seperated list) #subjectAltName_default = DNS:www.CertService.info
- countryName-国、国コードA2(ISO) www.worldatlas.com/aatlas/ctycodes.htm ;
- localityName-市;
- 0.organizationName-組織の名前。
- organizationalUnitName-組織の組織\組織;
- commonName-サーバーの場合、これはドメイン名、IPアドレスです。 ソフトウェアの場合-アプリケーションの名前、ユーザーの場合-フルネーム。 ルートおよび中間の場合、それらの名前。
- emailAddress-メール;
- subjectAltName-代替名(他のドメイン、メールなど);
- _default-デフォルト値を設定します。
それだけです、次に進みましょう。
拡張機能
次のいくつかのセクションは、証明書の作成に使用できる拡張機能です。 たとえば、-extensions root_caコマンドで引数を渡す場合、[root_ca]セクションが使用されます。
ルート証明書用
ルート証明書の場合、このセクションはroot_caと呼ばれます。
[ root_ca ] subjectKeyIdentifier = hash authorityKeyIdentifier = keyid:always,issuer basicConstraints = critical, CA:true keyUsage = critical, digitalSignature, cRLSign, keyCertSign
- subjectKeyIdentifier-サブジェクト識別子。 16進数の文字列(16進数)またはハッシュ(ハッシュ)にすることができます。
- authorityKeyIdentifier-このパラメーターは、keyidとissuerの2つの値のみを許可します。 Keyid-キーワードの識別子を親からコピーします。取得に失敗して常に存在する場合は、エラーが返されます。 発行者は、発行者(署名者)とシリアル番号を、署名された証明書からコピーします。 keyidが機能しない場合にのみ機能します。
- basicConstraints-CA-trueの場合、発行者になることができ、false-しない(明確にするために:issuer-エミッタ(署名者)、つまり証明書に署名できます);
- keyUsage-証明書でできること;
KeyUsageキー値|説明
--serverAuth SSL / TLS Webサーバー認証。
clientAuth SSL / TLS Webクライアント認証。
codeSigningコード署名。
emailProtection電子メール保護(S / MIME)。
timeStamping信頼できるタイムスタンプ。
msCodeInd Microsoft個別のコードスプーフィング(認証)。
msCodeCom Microsoft署名商用コード(認証)。
msCTLSign Microsoft信頼済み署名シート。
msSGC Microsoft暗号化セキュリティサーバー。
msEFS Microsoftファイルシステム暗号化。
nsSGC Netscape Server Gated Crypto。
中間証明書の場合
[ intermediate_ca ] subjectKeyIdentifier = hash authorityKeyIdentifier = keyid:always,issuer basicConstraints = critical, CA:true, pathlen:0 keyUsage = critical, digitalSignature, cRLSign, keyCertSign
重要な注意:
basicConstraintsパラメーターには、「pathlen:0」が含まれます。 pathlenは、チェーンのこの下に表示されるCAの最大数を示します。 したがって、ゼロポイントのCAがある場合、エンドユーザー証明書に署名するためにのみ使用でき、それ以上のCAには使用できません。
つまり、部門用、次にユーザー用の中間証明書を作成する場合は、pathlenを1に設定する必要があります。また、ゼロに等しいパラメーターを使用して、そのような証明書の拡張子を作成することをお勧めします。
最終証明書用
クライアント(認証およびメール用)
[ user_cert ] # ( basicConstraints = CA:FALSE nsCertType = client, email nsComment = "Client certificates" subjectKeyIdentifier = hash authorityKeyIdentifier = keyid,issuer keyUsage = critical, nonRepudiation, digitalSignature, keyEncipherment extendedKeyUsage = clientAuth, emailProtection
- nsCertType-証明書タイプ。 有効な値:client、server、email、objsign、reserved、sslCA、emailCA、objCA;
- nsComment-証明書へのコメント。
サーバー
[ server_cert ] # basicConstraints = CA:FALSE nsCertType = server nsComment = "Server Certificate" subjectKeyIdentifier = hash authorityKeyIdentifier = keyid,issuer:always keyUsage = critical, digitalSignature, keyEncipherment extendedKeyUsage = serverAuth
コードに署名するには
[ code_cert ] # basicConstraints = CA:FALSE nsCertType = server nsComment = "Code Certificate" subjectKeyIdentifier = hash authorityKeyIdentifier = keyid,issuer:always keyUsage = digitalSignature extendedKeyUsage = codeSigning, msCodeInd, msCodeCom
残り(詳細は後で)
[ crl_ext ] # authorityKeyIdentifier=keyid:always [ ocsp ] # OCSP (Online Certificate Status Protocol) basicConstraints = CA:FALSE subjectKeyIdentifier = hash authorityKeyIdentifier = keyid,issuer keyUsage = critical, digitalSignature extendedKeyUsage = critical, OCSPSigning
コンソールに行きます
基本的な構成を準備しました。コンソールにアクセスできます:)
作業ディレクトリを作成する
mkdir -p /root/ca/config mkdir -p /root/ca/{RootCA,PersonIntermediateCA,ServerIntermediateCA,CodeIntermediateCA}/{certs,crl,newcerts,private} mkdir -p /root/ca/{PersonIntermediateCA,ServerIntermediateCA,CodeIntermediateCA}/csr
すべての私権を公開します400
chmod 400 /root/ca/RootCA/private chmod 400 /root/ca/PersonIntermediateCA/private chmod 400 /root/ca/ServerIntermediateCA/private chmod 400 /root/ca/CodeIntermediateCA/private
構成ファイルを作成する
touch /root/ca/config/RootCA.cnf touch /root/ca/config/PersonIntermediateCA.cnf cp touch /root/ca/config/ServerIntermediateCA.cnf cp touch /root/ca/config/CodeIntermediateCA.cnf
Rootc.cnf [ ca ] default_ca = CA_default [ CA_default ] # , # ( ) dir = /root/ca/RootCA certs = $dir/certs private = $dir/private crl_dir = $dir/crl new_certs_dir = $dir/newcerts database = $dir/index.txt serial = $dir/serial RANDFILE = $dir/private/.rand # , , # ( - ) private_key = $private/RootCA.key.pem certificate = $certs/RootCA.cert.pem # crlnumber = $dir/crlnumber crl = $crl_dir/RootCA.crl.pem crl_extensions = crl_ext default_crl_days = 30 # default_md = sha256 name_opt = ca_default cert_opt = ca_default default_days = 365 preserve = no policy = policy_root [ policy_root ] countryName = match stateOrProvinceName = match organizationName = match organizationalUnitName = supplied commonName = supplied emailAddress = optional subjectAltName = optional [ req ] default_bits = 2048 distinguished_name = req_distinguished_name string_mask = utf8only default_md = sha256 # -x509. x509_extensions = root_ca [ req_distinguished_name ] countryName = Country Name (2 letter code) (C) countryName_min = 2 countryName_max = 2 countryName_default = RU stateOrProvinceName = State or Province Name (S) stateOrProvinceName_default = Krasnoyarskiy kray localityName = Locality Name (L) localityName_default = Norilsk 0.organizationName = Organization Name (O) 0.organizationName_default = CertService organizationalUnitName = Organizational Unit Name (OU) organizationalUnitName_default = CertService. IT-Department. commonName = Common Name (CN) #commonName_default = CertService.info emailAddress = Email Address emailAddress_max = 60 #emailAddress_default = support@CertService.info subjectAltName = Alternative DNS names (comma seperated list) #subjectAltName_default = DNS:www.CertService.info [ root_ca ] subjectKeyIdentifier = hash authorityKeyIdentifier = keyid:always,issuer basicConstraints = critical, CA:true keyUsage = critical, digitalSignature, cRLSign, keyCertSign [ intermediate_ca ] subjectKeyIdentifier = hash authorityKeyIdentifier = keyid:always,issuer basicConstraints = critical, CA:true, pathlen:0 keyUsage = critical, digitalSignature, cRLSign, keyCertSign [ crl_ext ] # authorityKeyIdentifier=keyid:always [ ocsp ] # OCSP (Online Certificate Status Protocol) basicConstraints = CA:FALSE subjectKeyIdentifier = hash authorityKeyIdentifier = keyid,issuer keyUsage = critical, digitalSignature extendedKeyUsage = critical, OCSPSigning
PersonIntermediateCA.cnf [ ca ] default_ca = CA_default [ CA_default ] # , # ( ) dir = /root/ca/PersonIntermediateCA certs = $dir/certs private = $dir/private crl_dir = $dir/crl new_certs_dir = $dir/newcerts database = $dir/index.txt serial = $dir/serial RANDFILE = $dir/private/.rand # , , # ( - ) private_key = $private/PersonIntermediateCA.key.pem certificate = $certs/PersonIntermediateCA.cert.pem # crlnumber = $dir/crlnumber crl = $crl_dir/PersonIntermediateCA.crl.pem crl_extensions = crl_ext default_crl_days = 30 # default_md = sha256 name_opt = ca_default cert_opt = ca_default default_days = 365 preserve = no policy = policy_intermediate_person [ policy_intermediate_person ] countryName = optional stateOrProvinceName = optional localityName = optional organizationName = match organizationalUnitName = optional commonName = supplied emailAddress = supplied subjectAltName = optional [ req ] default_bits = 2048 distinguished_name = req_distinguished_name string_mask = utf8only default_md = sha256 # -x509. x509_extensions = root_ca [ req_distinguished_name ] countryName = Country Name (2 letter code) (C) countryName_min = 2 countryName_max = 2 countryName_default = RU stateOrProvinceName = State or Province Name (S) stateOrProvinceName_default = Krasnoyarskiy kray localityName = Locality Name (L) localityName_default = Norilsk 0.organizationName = Organization Name (O) 0.organizationName_default = CertService organizationalUnitName = Organizational Unit Name (OU) organizationalUnitName_default = CertService. IT-Department. commonName = Common Name (CN) #commonName_default = CertService.info emailAddress = Email Address emailAddress_max = 60 #emailAddress_default = support@CertService.info subjectAltName = Alternative DNS names (comma seperated list) #subjectAltName_default = DNS:www.CertService.info [ root_ca ] subjectKeyIdentifier = hash authorityKeyIdentifier = keyid:always,issuer basicConstraints = critical, CA:true keyUsage = critical, digitalSignature, cRLSign, keyCertSign [ intermediate_ca ] subjectKeyIdentifier = hash authorityKeyIdentifier = keyid:always,issuer basicConstraints = critical, CA:true, pathlen:0 keyUsage = critical, digitalSignature, cRLSign, keyCertSign [ user_cert ] basicConstraints = CA:FALSE nsCertType = client, email nsComment = subjectKeyIdentifier = hash authorityKeyIdentifier = keyid,issuer keyUsage = critical, nonRepudiation, digitalSignature, keyEncipherment extendedKeyUsage = clientAuth, emailProtection [ crl_ext ] # authorityKeyIdentifier=keyid:always [ ocsp ] # OCSP (Online Certificate Status Protocol) basicConstraints = CA:FALSE subjectKeyIdentifier = hash authorityKeyIdentifier = keyid,issuer keyUsage = critical, digitalSignature extendedKeyUsage = critical, OCSPSigning
ServerIntermediateCA.cnf [ ca ] default_ca = CA_default [ CA_default ] # , # ( ) dir = /root/ca/ServerIntermediateCA certs = $dir/certs private = $dir/private crl_dir = $dir/crl new_certs_dir = $dir/newcerts database = $dir/index.txt serial = $dir/serial RANDFILE = $dir/private/.rand # , , # ( - ) private_key = $private/ServerIntermediateCA.key.pem certificate = $certs/ServerIntermediateCA.cert.pem # crlnumber = $dir/crlnumber crl = $crl_dir/ServerIntermediateCA.crl.pem crl_extensions = crl_ext default_crl_days = 30 # default_md = sha256 name_opt = ca_default cert_opt = ca_default default_days = 365 preserve = no policy = policy_intermediate_server [ policy_intermediate_server ] countryName = optional stateOrProvinceName = optional localityName = optional organizationName = match organizationalUnitName = optional commonName = supplied emailAddress = supplied subjectAltName = supplied [ req ] default_bits = 2048 distinguished_name = req_distinguished_name string_mask = utf8only default_md = sha256 # -x509. x509_extensions = root_ca [ req_distinguished_name ] countryName = Country Name (2 letter code) (C) countryName_min = 2 countryName_max = 2 countryName_default = RU stateOrProvinceName = State or Province Name (S) stateOrProvinceName_default = Krasnoyarskiy kray localityName = Locality Name (L) localityName_default = Norilsk 0.organizationName = Organization Name (O) 0.organizationName_default = CertService organizationalUnitName = Organizational Unit Name (OU) organizationalUnitName_default = CertService. IT-Department. commonName = Common Name (CN) #commonName_default = CertService.info emailAddress = Email Address emailAddress_max = 60 #emailAddress_default = support@CertService.info subjectAltName = Alternative DNS names (comma seperated list) #subjectAltName_default = DNS:www.CertService.info [ root_ca ] subjectKeyIdentifier = hash authorityKeyIdentifier = keyid:always,issuer basicConstraints = critical, CA:true keyUsage = critical, digitalSignature, cRLSign, keyCertSign [ intermediate_ca ] subjectKeyIdentifier = hash authorityKeyIdentifier = keyid:always,issuer basicConstraints = critical, CA:true, pathlen:0 keyUsage = critical, digitalSignature, cRLSign, keyCertSign [ server_cert ] # basicConstraints = CA:FALSE nsCertType = server nsComment = subjectKeyIdentifier = hash authorityKeyIdentifier = keyid,issuer:always keyUsage = critical, digitalSignature, keyEncipherment extendedKeyUsage = serverAuth [ crl_ext ] # authorityKeyIdentifier=keyid:always [ ocsp ] # OCSP (Online Certificate Status Protocol) basicConstraints = CA:FALSE subjectKeyIdentifier = hash authorityKeyIdentifier = keyid,issuer keyUsage = critical, digitalSignature extendedKeyUsage = critical, OCSPSigning
CodeIntermediateCA.cnf [ ca ] default_ca = CA_default [ CA_default ] # , # ( ) dir = /root/ca/CodeIntermediateCA certs = $dir/certs private = $dir/private crl_dir = $dir/crl new_certs_dir = $dir/newcerts database = $dir/index.txt serial = $dir/serial RANDFILE = $dir/private/.rand # , , # ( - ) private_key = $private/CodeIntermediateCA.key.pem certificate = $certs/CodeIntermediateCA.cert.pem # crlnumber = $dir/crlnumber crl = $crl_dir/CodeIntermediateCA.crl.pem crl_extensions = crl_ext default_crl_days = 30 # default_md = sha256 name_opt = ca_default cert_opt = ca_default default_days = 365 preserve = no policy = policy_intermediate_code [ policy_intermediate_code ] countryName = optional stateOrProvinceName = optional localityName = optional organizationName = match organizationalUnitName = optional commonName = supplied emailAddress = optional subjectAltName = optional [ req ] default_bits = 2048 distinguished_name = req_distinguished_name string_mask = utf8only default_md = sha256 # -x509. x509_extensions = root_ca [ req_distinguished_name ] countryName = Country Name (2 letter code) (C) countryName_min = 2 countryName_max = 2 countryName_default = RU stateOrProvinceName = State or Province Name (S) stateOrProvinceName_default = Krasnoyarskiy kray localityName = Locality Name (L) localityName_default = Norilsk 0.organizationName = Organization Name (O) 0.organizationName_default = CertService organizationalUnitName = Organizational Unit Name (OU) organizationalUnitName_default = CertService. IT-Department. commonName = Common Name (CN) #commonName_default = CertService.info emailAddress = Email Address emailAddress_max = 60 #emailAddress_default = support@CertService.info subjectAltName = Alternative DNS names (comma seperated list) #subjectAltName_default = DNS:www.CertService.info [ root_ca ] subjectKeyIdentifier = hash authorityKeyIdentifier = keyid:always,issuer basicConstraints = critical, CA:true keyUsage = critical, digitalSignature, cRLSign, keyCertSign [ intermediate_ca ] subjectKeyIdentifier = hash authorityKeyIdentifier = keyid:always,issuer basicConstraints = critical, CA:true, pathlen:0 keyUsage = critical, digitalSignature, cRLSign, keyCertSign [ code_cert ] # basicConstraints = CA:FALSE nsCertType = server nsComment = subjectKeyIdentifier = hash authorityKeyIdentifier = keyid,issuer:always keyUsage = digitalSignature extendedKeyUsage = codeSigning, msCodeInd, msCodeCom [ crl_ext ] # authorityKeyIdentifier=keyid:always [ ocsp ] # OCSP (Online Certificate Status Protocol) basicConstraints = CA:FALSE subjectKeyIdentifier = hash authorityKeyIdentifier = keyid,issuer keyUsage = critical, digitalSignature extendedKeyUsage = critical, OCSPSigning
すぐに使える構成アンダーデータベースを作成しましょう
touch /root/ca/RootCA/index.txt touch /root/ca/PersonIntermediateCA/index.txt touch /root/ca/ServerIntermediateCA/index.txt touch /root/ca/CodeIntermediateCA/index.txt echo 1000 > /root/ca/RootCA/serial echo 1A00000000000000 > /root/ca/PersonIntermediateCA/serial echo 1B00000000000000 > /root/ca/ServerIntermediateCA/serial echo 1C00000000000000 > /root/ca/CodeIntermediateCA/serial echo 1000 > /root/ca/RootCA/crlnumber echo 1FA0000000000000 > /root/ca/PersonIntermediateCA/crlnumber echo 1FB0000000000000 > /root/ca/ServerIntermediateCA/crlnumber echo 1FC0000000000000 > /root/ca/CodeIntermediateCA/crlnumber
証明書を使用します
ルート秘密鍵を作成する
openssl genrsa -aes256 -out /root/ca/RootCA/private/RootCA.key.pem 4096 chmod 400 /root/ca/RootCA/private/RootCA.key.pem
ルート証明書を作成する
openssl req -config /root/ca/config/RootCA.cnf \ -key /root/ca/RootCA/private/RootCA.key.pem \ -new -x509 -days 7300 -sha256 -extensions root_ca \ -out /root/ca/RootCA/certs/RootCA.cert.pem chmod 444 /root/ca/RootCA/certs/RootCA.cert.pem
証明書の有効性を確認する
openssl x509 -noout -text -in /root/ca/RootCA/certs/RootCA.cert.pem
中間物を作成し、ルートとして署名
# openssl genrsa -aes256 \ -out /root/ca/PersonIntermediateCA/private/PersonIntermediateCA.key.pem 4096 chmod 400 /root/ca/PersonIntermediateCA/private/PersonIntermediateCA.key.pem # openssl req -config /root/ca/config/PersonIntermediateCA.cnf -new -sha256 \ -key /root/ca/PersonIntermediateCA/private/PersonIntermediateCA.key.pem \ -out /root/ca/PersonIntermediateCA/csr/PersonIntermediateCA.csr.pem # openssl ca -config /root/ca/config/RootCA.cnf -extensions intermediate_ca \ -days 3650 -notext -md sha256 \ -in /root/ca/PersonIntermediateCA/csr/PersonIntermediateCA.csr.pem \ -out /root/ca/PersonIntermediateCA/certs/PersonIntermediateCA.cert.pem Using configuration from /root/ca/config/RootCA.cnf Enter pass phrase for /root/ca/RootCA/private/RootCA.key.pem: secret Check that the request matches the signature Signature ok Certificate Details: ... Sign the certificate? [y/n]:y 1 out of 1 certificate requests certified, commit? [y/n]y Write out database with 1 new entries Data Base Updated chmod 444 /root/ca/PersonIntermediateCA/certs/PersonIntermediateCA.cert.pem
残りの2つの中間体 # openssl genrsa -aes256 \ -out /root/ca/ServerIntermediateCA/private/ServerIntermediateCA.key.pem 4096 chmod 400 /root/ca/ServerIntermediateCA/private/ServerIntermediateCA.key.pem # openssl req -config /root/ca/config/ServerIntermediateCA.cnf -new -sha256 \ -key /root/ca/ServerIntermediateCA/private/ServerIntermediateCA.key.pem \ -out /root/ca/ServerIntermediateCA/csr/ServerIntermediateCA.csr.pem # openssl ca -config /root/ca/config/RootCA.cnf -extensions intermediate_ca \ -days 3650 -notext -md sha256 \ -in /root/ca/ServerIntermediateCA/csr/ServerIntermediateCA.csr.pem \ -out /root/ca/ServerIntermediateCA/certs/ServerIntermediateCA.cert.pem Using configuration from /root/ca/config/RootCA.cnf Enter pass phrase for /root/ca/RootCA/private/RootCA.key.pem: secret Check that the request matches the signature Signature ok Certificate Details: ... Sign the certificate? [y/n]:y 1 out of 1 certificate requests certified, commit? [y/n]y Write out database with 1 new entries Data Base Updated chmod 444 /root/ca/ServerIntermediateCA/certs/ServerIntermediateCA.cert.pem
# openssl genrsa -aes256 \ -out /root/ca/CodeIntermediateCA/private/CodeIntermediateCA.key.pem 4096 chmod 400 /root/ca/CodeIntermediateCA/private/CodeIntermediateCA.key.pem # openssl req -config /root/ca/config/CodeIntermediateCA.cnf -new -sha256 \ -key /root/ca/CodeIntermediateCA/private/CodeIntermediateCA.key.pem \ -out /root/ca/CodeIntermediateCA/csr/CodeIntermediateCA.csr.pem # openssl ca -config /root/ca/config/RootCA.cnf -extensions intermediate_ca \ -days 3650 -notext -md sha256 \ -in /root/ca/CodeIntermediateCA/csr/CodeIntermediateCA.csr.pem \ -out /root/ca/CodeIntermediateCA/certs/CodeIntermediateCA.cert.pem Using configuration from /root/ca/config/RootCA.cnf Enter pass phrase for /root/ca/RootCA/private/RootCA.key.pem: secret Check that the request matches the signature Signature ok Certificate Details: ... Sign the certificate? [y/n]:y 1 out of 1 certificate requests certified, commit? [y/n]y Write out database with 1 new entries Data Base Updated chmod 444 /root/ca/CodeIntermediateCA/certs/CodeIntermediateCA.cert.pem
検証を検証する
openssl verify -CAfile /root/ca/RootCA/certs/RootCA.cert.pem \ /root/ca/PersonIntermediateCA/certs/PersonIntermediateCA.cert.pem #result: /root/ca/PersonIntermediateCA/certs/PersonIntermediateCA.cert.pem: OK
証明書チェーンを作成してください
証明書チェーン-クライアントにルート証明書または中間証明書がない場合、このチェーンが必要です。
ADに何も追加しなかった場合、クライアントには最終的な+中間+ルートの束が必要です。
ADにルート証明書のみを追加する場合、リンクファイナル+中間の証明書チェーンが必要です。
中間証明書もADに追加される場合、証明書チェーンは不要です
cat /root/ca/PersonIntermediateCA/certs/PersonIntermediateCA.cert.pem \ /root/ca/RootCA/certs/RootCA.cert.pem > /root/ca/PersonIntermediateCA/certs/ca-chain.cert.pem chmod 444 /root/ca/PersonIntermediateCA/certs/ca-chain.cert.pem cat /root/ca/CodeIntermediateCA/certs/CodeIntermediateCA.cert.pem \ /root/ca/RootCA/certs/RootCA.cert.pem > /root/ca/CodeIntermediateCA/certs/ca-chain.cert.pem chmod 444 /root/ca/CodeIntermediateCA/certs/ca-chain.cert.pem cat /root/ca/ServerIntermediateCA/certs/ServerIntermediateCA.cert.pem \ /root/ca/RootCA/certs/RootCA.cert.pem > /root/ca/ServerIntermediateCA/certs/ca-chain.cert.pem chmod 444 /root/ca/ServerIntermediateCA/certs/ca-chain.cert.pem
部門ごとに1つの証明書を作成する
クライアント(-extensions
user_certを使用)
openssl genrsa -aes256 -out /root/ca/PersonIntermediateCA/private/User1.key.pem 2048 chmod 400 /root/ca/PersonIntermediateCA/private/User1.key.pem openssl req -config /root/ca/config/PersonIntermediateCA.cnf \ -key /root/ca/PersonIntermediateCA/private/User1.key.pem \ -new -sha256 -out /root/ca/PersonIntermediateCA/csr/User1.csr.pem openssl ca -config /root/ca/config/PersonIntermediateCA.cnf \ -extensions user_cert -days 375 -notext -md sha256 \ -in /root/ca/PersonIntermediateCA/csr/User1.csr.pem \ -out /root/ca/PersonIntermediateCA/certs/User1.cert.pem chmod 444 /root/ca/PersonIntermediateCA/certs/User1.cert.pem
サーバー(-extensions
server_certを使用)
openssl genrsa -aes256 -out /root/ca/ServerIntermediateCA/private/certservice.info.key.pem 2048 chmod 400 /root/ca/ServerIntermediateCA/private/certservice.info.key.pem openssl req -config /root/ca/config/ServerIntermediateCA.cnf \ -key /root/ca/ServerIntermediateCA/private/certservice.info.key.pem \ -new -sha256 -out /root/ca/ServerIntermediateCA/csr/certservice.info.csr.pem openssl ca -config /root/ca/config/ServerIntermediateCA.cnf \ -extensions server_cert -days 375 -notext -md sha256 \ -in /root/ca/ServerIntermediateCA/csr/certservice.info.csr.pem \ -out /root/ca/ServerIntermediateCA/certs/certservice.info.cert.pem chmod 444 /root/ca/ServerIntermediateCA/certs/certservice.info.cert.pem # - openssl rsa -in /root/ca/ServerIntermediateCA/private/certservice.info.key.pem -out /root/ca/ServerIntermediateCA/private/certservice.info.keynopass.pem chmod 400 /root/ca/ServerIntermediateCA/private/certservice.info.keynopass.pem
コードの場合(-extensions code_certを使用) openssl genrsa -aes256 -out /root/ca/CodeIntermediateCA/private/Calculator.key.pem 2048 chmod 400 /root/ca/CodeIntermediateCA/private/Calculator.key.pem openssl req -config /root/ca/config/CodeIntermediateCA.cnf \ -key /root/ca/CodeIntermediateCA/private/Calculator.key.pem \ -new -sha256 -out /root/ca/CodeIntermediateCA/csr/Calculator.csr.pem openssl ca -config /root/ca/config/CodeIntermediateCA.cnf \ -extensions code_cert -days 375 -notext -md sha256 \ -in /root/ca/CodeIntermediateCA/csr/Calculator.csr.pem \ -out /root/ca/CodeIntermediateCA/certs/Calculator.cert.pem chmod 444 /root/ca/CodeIntermediateCA/certs/Calculator.cert.pem
次の記事では、証明書を失効させ、OCSPを構成します。opensslののパラメータに関するソースとより:x509v3_config(英語)ルートのペアを作成します(。ENG)GitHubの(レディ)PS私は、右の瞬間のSSL-証明書を作成する方法を詳しく説明してみました。私はそのような記事がたくさんあることを理解していますが、記事が完全ではないことがよくあります。したがって、私はいくつかの部分で通常のフルバージョンを作成しようとします。私は多くの欠点があると思う、私はあなたのコメント、habrayuzeryに喜んでいるでしょう。